Sometimes Read and Write permissions that users get through authorization groups do not work properly on the file servers:
– Users without “Read” permissions can see folders
– Users without “Write” permissions can create folders
In this article I want to explain this problem a little bit more detailed and show you how to solve it. The reason the problem exists are the local groups “Users” and “Administrators” and their connections to the UAC. Why can I see folders without having permissions?
Index
In the last weeks I frequently had discussions about the two local groups Users and Administrators. Especially how they work together with the UAC (User Account Control) and NTFS permissions under Windows Server 2012R2 and Windows Server 2012R2.
Everything seems very clear, but it raises questions looking at it a second time.
Theory – Authorization Assignment for File Servers
The authorization for File Servers shall be assigned by the principle of the lowest common denominators between:
- Share authorizations and
- NTFS authorizations
If you assign read permissions on the share only, the access will be limited to „read“ at the maximum. This happens independently from the NTFS permissions, which could be wider here.
In practice, authorizations on the Share are usually set to “Change” access. NTFS permissions then control whether a user can “Change” oder “Read”.
In Practice – Share and File System Authorizations
In the following example I’d like to illustrate the problem of access authorizations for local groups a bit more.
- Create a share for the folder “D:\Data” with the name “Data”
- Create an authorization group „RF-Data-R“ in your Active Directory Domain
- Assign “Read” permissions to the group for the folder “D:\Data”
- Assign “Change” permissions to the share
- Create further sub folders and authorizations groups if you like
ABE (Access Based Enumeration) is activated for this share. A users account becomes member in various groups, including the group “RF-Data-R”.
You expect, that:
- the user can only see the folders with ABE,
the user has permissions for (based on its authorization group memberships) - the user has „Read“ permissions for the folders,
the user has „Read“ authorizations (based on its authorization group memberships)
meaning: that these permissions take effect
You will note, that:
- the user can see all folders,
whether or not the user has the permissions. The folders should be made invisible by ABE - the user can create folders and files,
with „Read“ only permissions from the authorization group.
The Authorization Conflict Explained
A look at the NTFS permissions reveals why it turned out differently.
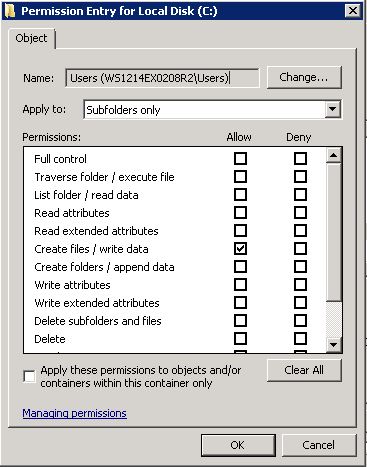
By default, the local group “Users” is authorized to access on any NTFS volume.
The group has the permission “Read & Execute” and the special authorization to “Create files / write data“.
Your first thought might be:
“The users is not member of the file servers local group” – but that is actually not true.
Having a look in the MSDN Library for local standard groups explains why:
Local Group Users:
” By default, the Domain Users, Authenticated Users, and Interactive groups are members of this group. Therefore, any user account created in the domain becomes a member of this group.”
Solution for the Local Group Users
The solution is simple. Just remove the permission of the local “user” on the top level of new NTFS volumes – before you start setting up the folders and shares.
Unfortunately, this solution brings a new component into play: UAC.
UAC – User Access Control
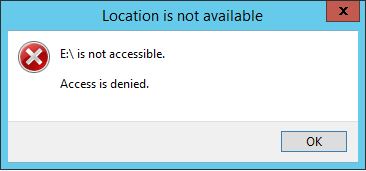
Having removed the local group “Users” from the NTFS ACLs (and restarted the RDP session to your new file server), you will note that you no longer have access to the folders. Check the membership in local Administrators and you may wonder.
SID of the Local Group Administrators missing
The reason is that UAC removes the SID of the local Administrators group from the access token during the registration via RDP. This is why you are no longer an administrator. Many administrative tools automatically run a query whether you want to run the program with privileges, or start it directly by right-clicking with the “Run as administrator“. The Windows Explorer is always running in the context of the logged-on user, a “Run As” does not exist here.
This explains the strange behaviour
- No local Administrator because of UAC
- No NTFS authorization for the local group Users (removed before)
- Result: no access to folders of the NTFS Volumes
Solution 1 – Administrative Domain Group
There is a simple solution for the UAC. I recommend to define a domain administrative group, which you can delegated for the administration of file services. This file admin group is member of the Local Administrators group and receives “Full Control” on the NTFS volume. In addition, we give this group “Full Control” permissions to the share to ensure that the NTFS permissions can be managed over the network.
Solution 2 – Disable UAC
There is a more radical way to deal with the UAC problems. You can disable the UAC in the Windows registry. I do not recommend this! Nevertheless I want to mention it for completeness here:
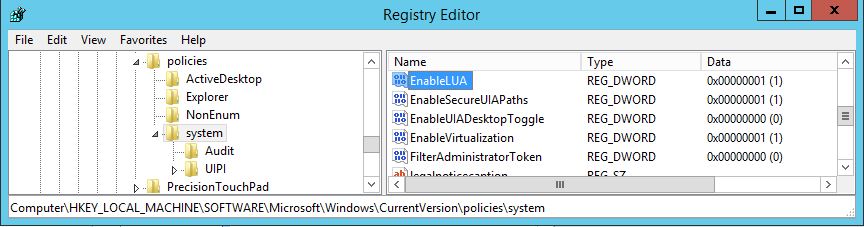
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System
UAC aktivieren: EnableLUA = 0x00000001
UAC deaktivieren: EnableLUA = 0x00000000
With solution 1 or 2 the permissions on the local Users group on NTFS should then work correctly
Please contact us for further information.








Leave a Reply
<p>Your email is safe with us.<br/>Information about our <a href="https://activedirectoryfaq.com/contact-us/">data protection policies</a></p>