Active Directory Delegation with DSACLS
DSACLS means Domain or Directory Services Access Control Lists. The tool is based on command lines and serves the control of access authorizations.
During many Active Directory migration-projects not only the pure user data-migration is performed but also a reorganization of the administrational concept. For this, delegation rights to the newly designed organizational structures have to be implemented in the Active Directory.
In the following I will present possibilities of delegation. Then I’ll give some examples with DSACLS.
Index
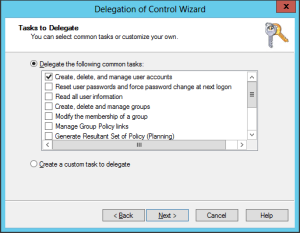
Delegation with the Delegation of Control Wizard
The delegation of Control Wizard of Active Directory Users und Computers Console is surely be known among most administrators.
Advantage: The Wizard is rather comfortable and very helpful for the occasional delegation with standard authorizations.
Disadvantage: For the building up of a delegation structure the Wizard is too fiddly and cannot be granularly adjusted enough.
Delegation structures with DSCALS
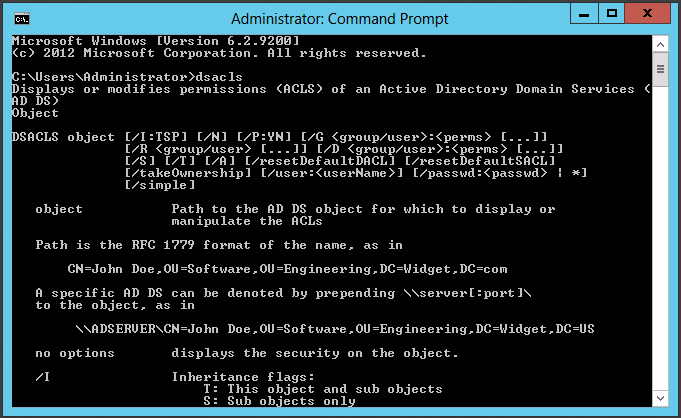
Another possibility is the Command Line Tool DSACLS.exe. This tool is integrated from Windows Server 2008 on and available with the installation of the AD DS Server Role.
The tool has to run in a Command Console which was started as admin. Then Grant/ G or Deny/ D rights can be set for groups and users on any Active Directory object. Different options ranging from total access to granting of writing authorizations to individual attributes can then be entered.
The basic syntax is:
|
1 |
Dsacl „Objekt-DN“ /I:[T|S|P] /G <PermissionStatement> [<PermissionStatement>] |
A permission statement is designed after the syntax:
|
1 |
User|Group:Permission:ObjectType|Property |
You can find a detailed description of the syntax with all options in Microsoft’s Technet.
Note for the conception of delegation authorizations
Authorizations should whenever possible be granted additively, meaning that certain roles should be assigned with exclusively more authorizations (writing authorizations). It should be avoided to deal out Deny-authorizations because the Active Directory is a basically informing directory in which every member has reading authorizations on a lot of information by default. Thus, it should be avoided to limit this reading access because it could lead to unpredicted side effects.
Examples for the use of DSACLs
I will explain the use of DSACLs on the following two examples:
- The user- and authorizations-administration should be able to create new users
- The Helpdesk should be able to reset passwords
User- and authorizations-administration – user set up
In case the user- and authorizations-administration is to be granted the right to set up new users, it should look like this:
|
1 |
<strong>dsacls "ou=users,ou=de,ou=corp,dc=contoso,dc=com" /I:T /G "CONTOSO\AR-BBV-DE:CC;user"</strong> |
It grants the group AR-BBV-DE on the OrganizationsUnit ‘ou=users,ou=de,ou=corp,dc=contoso,dc=com’ the right to create Child-objects of the type User (CC: Create a child object). The heredity /I:T means that this right is inherited to the OU and all sub objects.
HelpDesk – password reset and unlocking
In this example the authorizations for resetting passwords and unlocking user-accounts is granted to HelpDesk.
|
1 |
<strong>dsacls "ou=corp,dc=contoso,dc=com" /I:S /G "CONTOSO\AR-HELPDESK-ALL:CA;Reset Password;user" "CONTOSO\AR-HELPDESK-ALL:WP;pwdLastSet;user" "CONTOSO\AR-HELPDESK-ALL:WP;lockoutTime;user"</strong><strong> </strong> |
With CA (Control Access) access to an expanded right is granted (to ‘reset password’). With the command WP (write to a property) the property „pwdLastSet“ can be inscribed by HelpDesk. Thus, it can command the user to change his or her password at next login. For this, the value of Users and Computers Console is set to 0. With the right for inscribing the property “lockoutTime” HelpDesk can unlock a user by setting “lockoutTime” to 0.
Conclusion
Both examples already describe how powerful and flexible DSACLS is.
It can be used for:
- OrganizationalUnits
- Containers
- Every object type contained in the Active Directory scheme
Authorizations can be set generally or on individual attributes, with every heredity-mode.
Once the delegation-structure is planned conceptually, DSACLS offers an easy way to transfer the concept into unambiguous technical rules. Like this, for every delegation role e.g. an authorization-template can be created as CMD-script. It can be reused for every new suborganisation. Additionally, the templates are a good backup to be able to restore hidden authorizations out of the delegation concept.
For delegation of user-set up or other routine tasks the program FirstWare-Admin has proven quite flexible and efficient.








1 Comment
Leave your reply.