Last week I faced the easy task to activate LDAPs on Windows Server 2008 R2 domain controllers. One of the applications required an encrypted LDAP connection, because password changes are done via LDAP.
I thought: Hey, that’s easy – just create a server certificate for the DC, import the certificate for the computer account under ‘personal’ via MMC – and done.
Apparently it is not that easy with Windows Server 2008 / 2008 R2 …
Index
LDAPs with Server 2008
To establish LDAP over SSL, I did what I mentioned above.
I created a server certificate for the DC. Then tried to import it to the “personal” settings of the computer account.
Port 636 for LDAPs was activated on the DC with the installed server certificate.
A Telnet connection was also possible.
But, unfortunately a LDAPs connection with the application server could not be achieved
(Yes, the root certificate was installed on the application server).
After researching the problem I found out that a change was introduced with Windows Server 2008 / 2008 R2:
The server certificate has to be imported into the ‘AD DS personal store’.
Import server certificate to AD DS personal store
Here is a step by step manual for the import of the certificate:
- MMC Console / Add or Remove Snap-Ins / Certificates
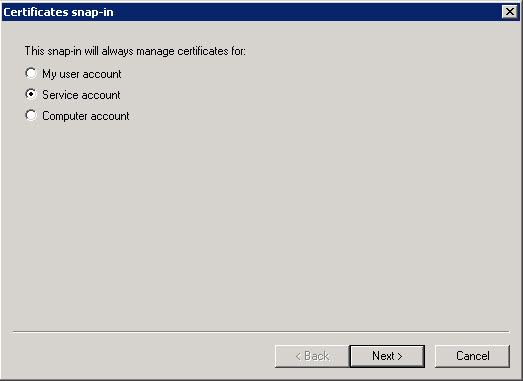
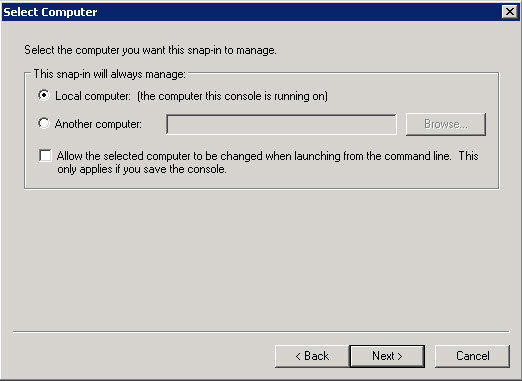
- Select Computer: Local Computer
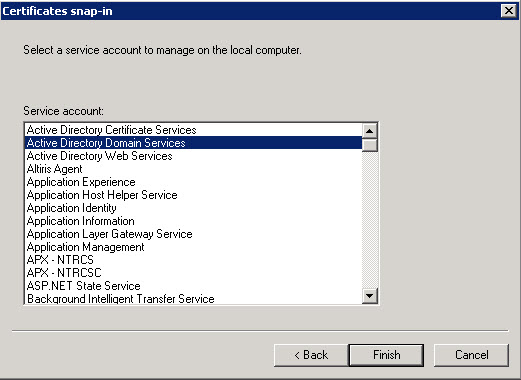
- Select Service Account: Active Directory Domain Services
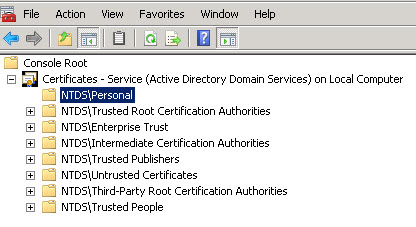
- The certificate is being imported into the Store ‘NTDS\Personal’
Link to the Microsoft Technet article: LDAP over SSL








1 Comment
Leave your reply.