In Azure Active Directory (Azure AD), there are different types of groups that are used for different purposes. In this article, we will explain the different groups and their functions. There are mainly two different group types, security groups and Microsoft 365 (M365) groups, for which there are in turn subtypes that offer different possibilities. We will go into more detail in the next sections.
Index
Differences between groups in on-premises AD and Azure AD
Active Directory and Azure Active Directory are both directory services from Microsoft. They are used to manage user accounts and access rights. Active Directory is mainly used in local networks. Azure AD, the cloud-based directory service, takes care of managing identities on Microsoft’s Azure cloud platform. In hybrid scenarios, local ADs are used in conjunction with Azure AD, often together with synchronization of the two directories.
The functionality of groups in both services is similar, but there are differences in management and handling. In Active Directory, there are security groups and distribution groups. Security groups you use for access to resources. Distribution groups are used for email distribution lists. Azure AD, on the other hand, offers security groups as well as Microsoft 365 (M365) groups, device security groups and application security groups. M365 groups are groups hosted in the cloud. They have an email address and a collection of online resources.
Security groups in Azure AD
Security groups are primarily used by Azure AD to grant or deny access rights to resources in Azure and its associated services. For example, membership in a security group can be used to control access to an application, SharePoint site, or file share. These groups can be used by users to send emails to a group of users in Exchange Online.
Security groups in Azure AD differ between dynamic groups and synchronized groups. In the “Assigned” membership type, admins permanently assign users to groups, similar to Active Directory.
M365 groups play an important role in Azure AD
For Microsoft 365, Azure AD plays an important role because the authentication of users is done via user accounts in Azure AD. In this context, M365 groups are also interesting.
M365 groups are used to create a group of users and grant access to specific M365 resources such as SharePoint sites, Teams and other resources. So basically, an M365 group is also a security group, but with more features. They come into play when using M365, especially when different users work together in shared teams on resources that are in turn built on services in M365, for example Exchange Online or SharePoint Online.
Managed (dynamic) and synchronized groups
The differences between these two types of groups are significant, which is why we are looking at them individually.
Managed or dynamic groups
How it works
Managed groups (dynamic groups) are groups whose membership is based on rules. For example, you can create a rule that says that all users with an email address ending with “@yourcompany.com” are members of the group. When admins add a new user and their email address matches this rule, Azure AD automatically adds the user to the group. This is possible for both security groups and M365 groups.
In turn, Azure AD automatically removes a user who no longer meets the specified conditions from the group. For example, a rule can specify that all users with a certain role or attribute, for example all members of the marketing department, should be members of a certain group. Maintenance is automatic; admins do not have to assign users manually.
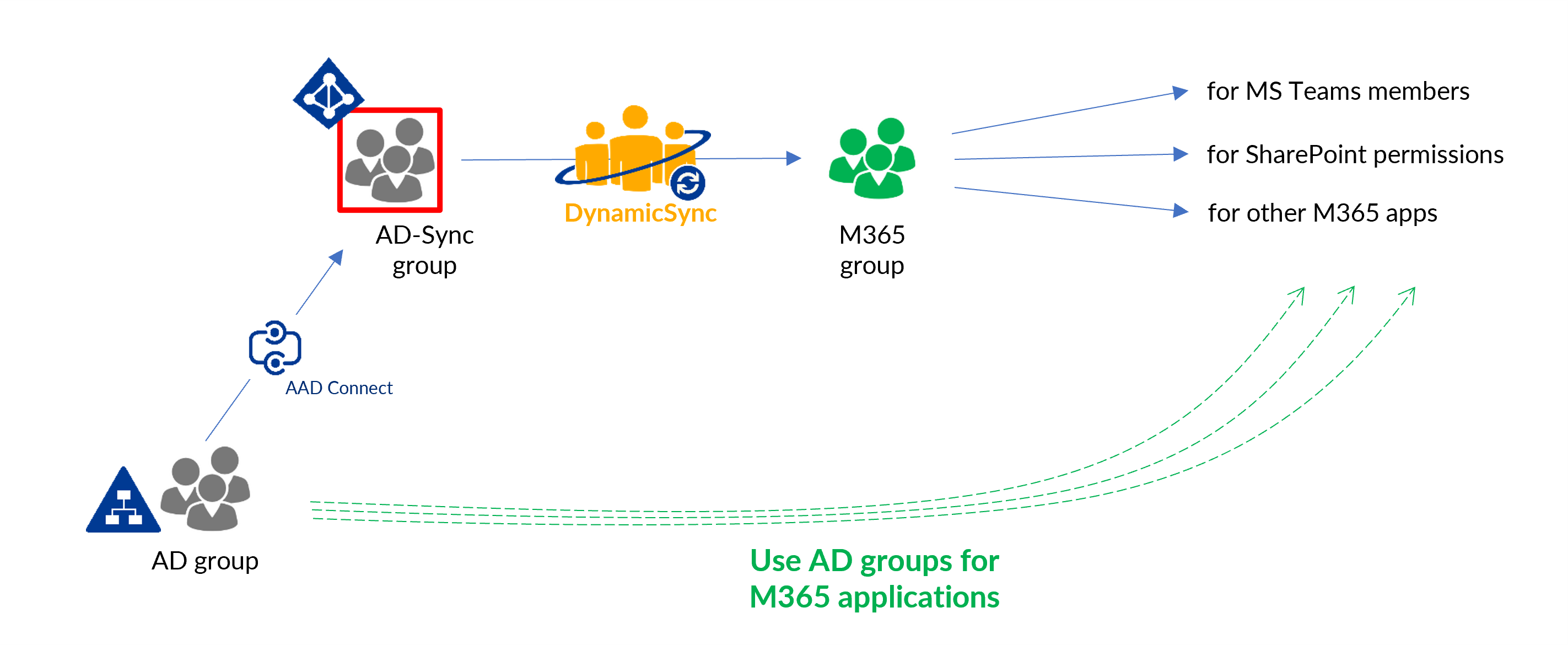
To use dynamic groups, an Azure AD P1/P2 license per user is required. An alternative are dynamic AAD groups created with DynamicSync. Here more attributes are selectable and features like include or exclude lists are included.
Using dynamic groups in Azure AD
Dynamic groups in Azure AD provide flexible and automated management options for group memberships and are particularly useful for several use cases:
Automated access control: Dynamic groups allow you to automatically control access to resources based on user attributes. For example, you can create a dynamic group that includes all members of a specific department or role and allow that group to access relevant resources.
User management: Dynamic groups simplify the management of large numbers of users. In particular, if users move frequently between departments, dynamic groups update membership automatically, eliminating the need for manual adjustments.
License management: Azure AD enables licensing based on group memberships. Dynamic groups enable automatic assignment and management of licenses based on user attributes.
Security and compliance: Dynamic groups help enforce security policies and support compliance requirements. For example, you can create a dynamic group that includes all users with administrative privileges. This ensures that only authorized users have access to sensitive resources.
Synchronized groups
How it works
Synchronized groups originate from an on-premises Active Directory environment and are synchronized from there with Azure AD. In the management of these groups, the value “Windows Server AD” can be found under “Source”.
Typically, admins manage membership in these groups locally and then synchronize them with the cloud. So when you make a change to group membership, it is first done in the on-premises Active Directory environment. Then Azure AD Connect replicates the changes to Azure AD. This type of group is often used by organizations when they are using a hybrid identity solution where some or all user identities are managed both on-premises and in the cloud. Both types of groups offer their own use cases and can be selected based on an organization’s specific needs and infrastructure.
Synchronized groups important for hybrid IT environments
Connection between Active Directory and Azure AD
Synchronized groups in Azure AD typically originate in on-premises Active Directory environments and play a critical role in hybrid IT environments. They enable seamless integration between on-premises AD and Azure by synchronizing user identities, group memberships, and associated attributes.
For synchronization, use tools such as Azure AD Connect or Azure AD Connect Cloud Sync. These tools are provided by Microsoft to connect between on-premises Active Directory and Azure AD. The tools synchronize not only groups and users, but also passwords, which improves the user experience by enabling a common identity for users locally and in the cloud.
Important points for on-premises and cloud synchronization
However, administrators should keep a few points in mind when synchronizing. First, they must ensure that the on-premises Active Directory objects that are to be synchronized meet Azure AD requirements, for example, in terms of allowed characters in user names. In addition, note that changes to group memberships or user attributes are made in the on-premises Active Directory environment and then synchronized with Azure AD. This means that administrators who are used to making changes directly in the cloud will have to get used to this workflow. Solutions like DynamicSync from FirstAttribute make synchronization much easier to control. More on this in the next section.
Finally, it is important to pay attention to the synchronization intervals. By default, synchronization occurs every 30 minutes, but depending on the specific needs of the organization and the size of the environment, it may be necessary to adjust this interval. Overall, synchronized groups provide a powerful way to manage hybrid identities and ensure a consistent user experience across on-premises and cloud environments.
For efficient use of synchronized groups between AD and Azure AD, as well as non-disruptive user login to Active Directory and Azure AD, we recommend reading “Azure AD Connect and Azure AD Connect Cloud Sync” and “Install Azure AD Connect” where we discuss the capabilities provided by Microsoft.
Synchronize groups efficiently with DynamicSync
To avoid confusion in Azure AD groups, add-on tools like DynamicSync from FirstAttribute can be of great help. They enable dynamic management of groups in the cloud, similar to dynamic groups in Azure AD. DynamicSync, which runs entirely in the cloud and requires no on-premises installation, offers key advantages:
It does not require a P1 subscription to Azure AD and provides wide-ranging functionality at a lower cost. In addition, DynamicSync extends the capabilities of group-based synchronization. The solution can synchronize different types of cloud groups with other groups and access already synchronized groups, M365 groups and security groups in AD.
DynamicSync not only creates traditional static group memberships in Active Directory dynamically in Azure AD, but can also create attribute-based groups. These form the group memberships using user fields and attributes. With the stored attributes and fields, DynamicSync can create new groups in Azure AD and new teams in M365.
RBAC and ABAC authorization concepts in Azure AD
In Azure AD, there are several concepts for managing permissions. Two of the most important are Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC).
RBAC is a role-based authorization system. Users or groups are assigned roles, and each role has specific permissions. When you assign a role to a person, he or she receives all the permissions associated with that role. For example, Azure AD uses RBAC to manage access to resources in Azure.
ABAC is an extended model based on attributes. With ABAC, you can create policies that control access to resources based on attributes of users and resources. This can provide very fine-grained control, but can also be more complex than RBAC. ABAC is particularly useful in situations where access to resources depends on dynamic factors that can be expressed by user attributes such as location, time of day, role, or other attributes.
Summary
Groups in Azure AD are not direct alternatives to RBAC and ABAC, but complement these concepts. Groups help simplify the management of users and their access rights. For example, you can use groups to define a group of users and then assign roles and permissions to them collectively through RBAC. Or you can use attributes of groups in ABAC policies to control access to resources.
In summary, RBAC, ABAC, and groups in Azure AD can work together to create a flexible and powerful system for managing access rights. It is important to understand each of these concepts and how they can best be used in different scenarios.
Dear readers of the ADFAQ blog. Thank you for your interest in our articles. Our experts write these articles to the best of their knowledge, but the world of IT changes quickly. As a rule, we do not update the written blogs or rather rarely. Therefore, we cannot guarantee that the content is always up to date. Here, you can find a link to the our tool that creates dynamic groups in Azure AD, DynamicSync.
FirstAttribute AG – Identity Management & IAM Cloud Services
We would be happy to present our services and solutions to you. Get in touch and find out how we can help you.








Leave a Reply
<p>Your email is safe with us.<br/>Information about our <a href="https://activedirectoryfaq.com/contact-us/">data protection policies</a></p>