The installation of an application requires elevated rights. At first, the administrator might try to decline the request. But quite often colleagues return with an “approval” by their management. If you like it or not, you have to set up the permissions. Most likely, you do it on condition that these will just be temporary permissions. However, only the most thorough administrators will remember to revoke these permissions at a later date.
This problem can be solved with temporary permissions which delete themselves automatically. In this article I will show you how to implement these permission in Active Directory.
Index
A solution to temporary permissions
Let us continue with our example and assume that the application creates new Service Connection Points (SCPs). The account through which the application is installed requires domain admin rights. In order to allow for temporary permissions we create a group which is automatically deleted after a certain lifetime (TTL, time-to-live). This group could become a member of the domain admins. The accounts through which the application is installed become members of this temporary group. After the TTL has expired the group is automatically deleted and the user accounts lose their domain admin rights.
Temporary groups
Here is a summary of the most important facts about temporary groups:
- Temporary objects have been available in Active Directory since version 2003.
- They cannot be created with standard Active Directory cdmlets, instead they require an ADSI interface.
- The groups are created as the objectClass “dynamicObject” which means that they are deleted during the Garbage Collection Process (similar to Tombstone Objects).
- Therefore, these temporary groups have no tombstone and cannot be reactivated.
- This also means you cannot transform existing groups into temporary groups and vice versa.
- Minimum lifetime interval = 15 minutes
- Maximum lifetime interval = 1 year
Creating a temporary group
As mentioned above, you can create temporary groups via an ADSI interface or via a LDIF import. I chose PowerShell as my approach.
Defining the TTL interval
The system displays the TTL interval in seconds. For more covenient data entry the time is entered in minutes and then converted into seconds. In our example the TTL interval is set to 15 minutes.
|
1 2 |
[INT]$TTLminutes=15 $TTLSeconds = [int](New-TimeSpan -minutes $TTLminutes).TotalSeconds |
Linking an OU object via ADSI
In order to create objects with ADSI you apply the “.create” method on the OU object. First, you have to bind the OU as an object:
|
1 2 |
$destinationOu="OU=TempGroups,DC=JKDOM,DC=NET" $destinationOuObject = [ADSI]("LDAP://JK-DC01.JKDOM.NET/" + $destinationOu) |
Adding a temporary group to domain admins
Since we want to add a group to the domain admins group we have to select the group type “global group“. Please note that you cannot add domain local groups or universal groups to global groups of the same domain. (Here is an article that dives deeper into this topic: Group Nesting in Windows Domains). In line 3 you set”objectClass = dynamicObject“. To be as precise as possible you write down the time of deletion in the description.
|
1 2 3 4 5 6 7 8 |
$GroupName="TempDomainAdmin" $TempGroup = $destinationOuObject.Create("group","CN=$GroupName") $TempGroup.PutEx(2,"objectClass",@("dynamicObject","Group")) $TempGroup.Put("entryTTL",$TTLSeconds) $TempGroup.Put("sAMAccountName", $GroupName) $TempGroup.Put("displayName", $GroupName) $TempGroup.Put("description",("Temp Group, will be deleted automatically on " + $RemoveTime.ToShortDateString() +" at "+ $RemoveTime.ToShortTimeString() )) $TempGroup.SetInfo() |
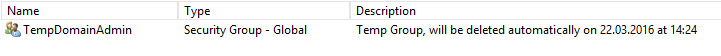
The final group
So, we created a global group which will expire automatically on March 22nd, 2016 at 02:24 p.m..
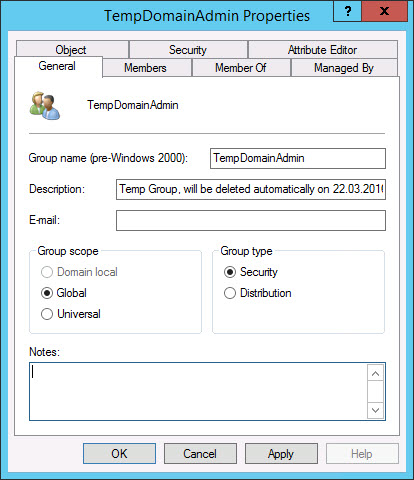
Additionally, the new temporary group can be managed via the “Active Directory Users and Computers” console:
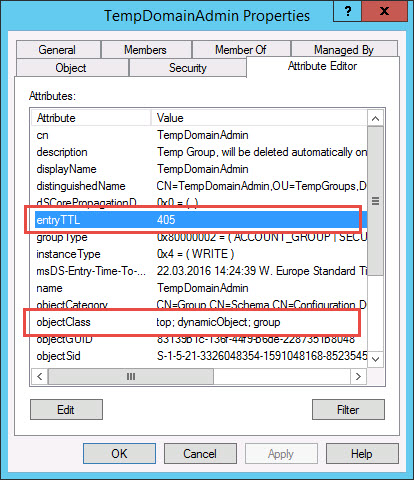
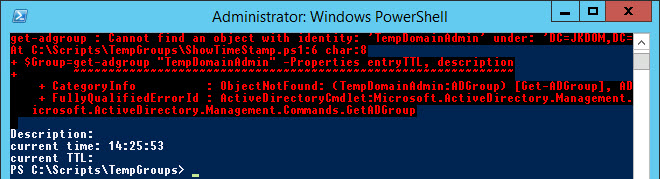
The field “entryTTL” shows the TTL interval of the group and the field “objectClass” displays “dynamicObject“.
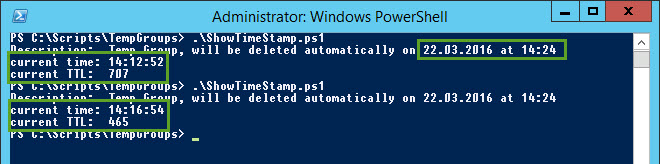
Here follows the script which shows the definition of the TTL:
At 02:25 p.m. the garbage collection automatically deleted the group already. Thus the PowerShell script cannot bind the group anymore:
Summary
By using the objectClass “dynamicObject” you can set temporary permissions in Active Directory.
Temporary permissions with dynamic groups
There are of course further ways to create temporary group permissions.
We developed the software solution FirstWare DynamicGroup to make dynamic group memberships available in Active Directory.
To set up a temporary group membership with DynamicGroup you need
- user objects (other objects work as well)
- a time attribute, with syntax “UTC coded time” like expiration time (examples only, you should choose attributes that do not end the account 😉 )
- LDAP converted time stamp for date the permission should end (this tool helps converting YMD LDAP)
- DynamicGroup 2018 or newer
For more information about DynamicGroup and our consulting performance, please contact us.
FirstAttribute AG – Identity Management & IAM Cloud Services
We would be happy to present our services and solutions to you. Get in touch and find out how we can help you.







4 Comments
Leave your reply.