Hybrid onboarding refers to the process of integrating new users into both on-premises Active Directory (AD) environments and cloud-based identity services such as Microsoft Entra ID. In today’s increasingly hybrid IT infrastructures, onboarding involves not only creating user accounts and assigning access rights in AD, but also synchronizing these identities with Entra ID. Furthermore, more and more companies are moving from mixed administration to purely cloud-based administration.
Hybrid onboarding is therefore an essential process to ensure that users can work quickly and securely across an organization’s entire IT landscape without risking security breaches that may arise from inconsistent or manual processes. The following article shows what administrators should pay attention to during this process.
Index
What is important in a hybrid IT environment?
In a hybrid IT environment, it is crucial to pay particular attention to data synchronization and avoiding duplicate data maintenance, especially when onboarding new users. One of the key challenges is to ensure that all user data and permissions are consistently synchronized between the different systems.
Administrators must ensure that users are seamlessly set up in both on-premises and cloud systems, which requires precise configuration of synchronization services such as Entra Connect or Entra Cloud Sync. Here you will find an article on this topic that is well worth reading, which compares the two services: Entra Connect v2 vs. Entra Cloud Sync
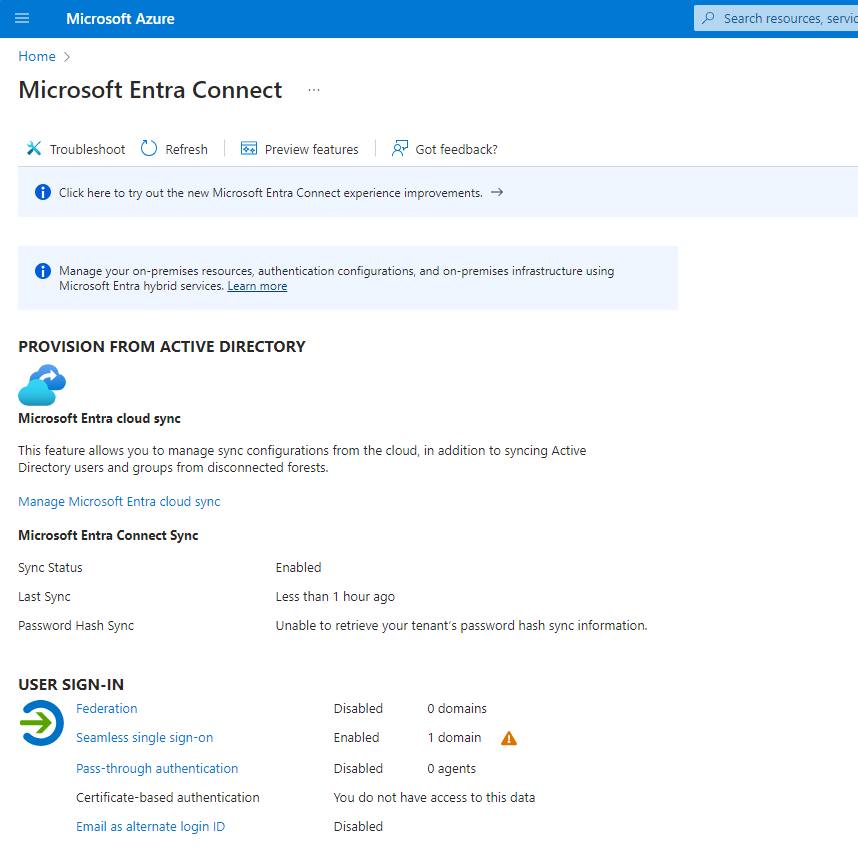
This prevents user data from being updated in one system without the changes being reflected in the other. Such discrepancies can lead to inconsistencies and potential security vulnerabilities. To minimize these risks, administrators must ensure that all identity data is synchronized in real time between AD and Entra ID.
Which directory should be used
On-premises environments
One of the key questions when onboarding is which directory (AD or Entra ID) should be used as a priority.
In traditional on-premises environments, Active Directory is often the primary directory, as it forms the basis for managing users, computers and groups in the corporate network. Here, onboarding typically occurs by creating a new user account in AD, after which that account is replicated to the cloud through synchronization tools such as Entra ID Connect or Entra Cloud Sync. Entra ID handles the management of cloud-specific access rights and services, such as access to Microsoft 365.
Cloud-based environments or ‘cloud-first’ strategy
In purely cloud-based environments, on the other hand, Entra ID is the primary directory. Here, onboarding takes place directly in the cloud, and synchronization with on-premises directories is only performed when necessary. This approach can be useful in companies that follow a “cloud-first” strategy or that only operate a small amount of on-premises infrastructure.
The decision on whether to prioritize AD or Entra ID depends on the organization’s specific IT strategy. In most mixed environments, AD continues to be used as the primary directory, as it forms the basis for managing on-premises infrastructure. Entra ID is used for extension to the cloud, enabling organizations to benefit from both worlds.
Recommendation for mixed environments
A recommended approach for a hybrid IT infrastructure is to initially perform the onboarding in AD, as this creates a consistent basis for synchronization with Entra ID. This minimizes the risk of synchronization problems and ensures that all permissions and access are correctly mapped in both systems. IAM solutions, such as the FirstWare IDM-Portal, can greatly simplify this process by enabling centralized administration and automation of onboarding in both directories.
One way could also be to use Entra ID as the primary identity source if the company has a strong cloud orientation and only minimal on-premises infrastructure. This enables more efficient use of cloud capabilities and easier management of identities and access rights, especially in large, distributed environments.
Differences in onboarding in AD and Entra ID
Here is a table describing the differences in onboarding in Active Directory and Entra ID:
|
Characteristic |
Active Directory (AD) |
Entra ID (Azure AD) |
|
Primary directory |
On-premises infrastructure, often used by companies with on-premises systems |
Cloud-based infrastructure, particularly in “cloud-first” strategies |
|
Onboarding process |
User accounts are created and managed directly in AD. |
User accounts are created and managed directly in Entra ID. |
|
Synchronization |
User accounts and permissions must be replicated to the cloud (via Entra ID Connect) |
Synchronization with AD is only necessary for hybrid scenarios. |
|
Access management |
Management of local network resources and applications |
Management of cloud-based resources such as Microsoft 365 |
|
Group memberships |
AD groups control access to on-premises resources |
Entra ID groups manage access to cloud applications and services |
|
Automation |
Manual processes dominate, with few integrated automation tools |
Higher level of automation through cloud-based tools and scripting options |
|
Compliance and auditing |
Limited native audit capabilities, often requiring external tools |
Comprehensive built-in audit and reporting capabilities for cloud compliance |
|
Resource availability |
Resources and services are available and administered locally |
Resources and services are available globally and administered via the cloud |
|
Best practices |
AD should often be used as the primary directory in hybrid environments. |
Entra ID could be used as the primary identity source if there is a “cloud-first” strategy. |
In addition to onboarding, offboarding is also important for companies from a security perspective, especially with regard to access permissions. Find out more about the key differences between offboarding in Entra ID and AD, as well as best practice tips, in our article “Hybrid offboarding in Entra ID and Active Directory”.
Hybrid Authentication and SSO
When implementing SSO in hybrid environments, it is crucial to ensure seamless and secure authentication for both on-premises and cloud-based resources. This requires that authentication protocols such as OAuth 2.0 and OpenID Connect in Entra ID be configured correctly. These configurations are necessary to enable SSO. At the same time, the integration of local authentication methods, such as Kerberos or NTLM in AD, should be designed to be compatible with Entra ID requirements.
In addition, setting up multi-factor authentication (MFA) in both environments is essential to increase security. It also helps ensure protection against phishing and other threats. When configuring SSO, administrators must ensure that all identity and resource providers communicate correctly with each other. They must also ensure that tokens are exchanged securely.
In AD, it is important that all access rights and group memberships are regularly reviewed and updated to ensure that users have only the minimum necessary rights. Configuration of Group Policies (GPOs) should also be undertaken to support organizational security policies, particularly around password requirements and account lockout policies.
In Entra ID, on the other hand, special attention should be paid to the configuration of conditional access policies. These make it possible to control access to cloud resources based on certain conditions, such as location or device. In addition, it is crucial that the synchronization between AD and Entra ID works seamlessly, which is ensured by the correct configuration of Entra Connect. In doing so, administrators must ensure that there are no synchronization conflicts that could lead to inconsistencies in user profiles.
Equally important is the regular review of audit logs and security alerts in both environments. Regular monitoring enables early detection and response to potential security incidents.
Onboarding in Active Directory
Onboarding in Active Directory often occurs through the Active Directory Users and Computers (ADUC) tool, which allows administrators to create new user accounts, add them to groups, and manage access rights to network resources. The process begins with the creation of a new user account, which involves defining important details such as username, password, and organizational unit (OU). Group memberships and permissions can then be assigned to ensure that the user has access to the resources they need.
One of the biggest challenges is the manual administration of user accounts and permissions. This can lead to errors, such as incomplete or inconsistent permission assignments, which can compromise network security. In addition, in complex environments it can be difficult to keep track of all group memberships and delegated rights, which increases the risk of overlooked security vulnerabilities.
The FirstWare IDM-Portal from FirstAttribute AG offers a solution here by automating and centralizing user administration. It enables administrators to create and manage user accounts more efficiently while ensuring that all necessary security policies are adhered to. By automating tasks such as assigning group memberships and managing access rights, the IDM portal reduces the potential for errors and improves security. It also offers comprehensive audit and reporting functions that enable transparent tracking of all changes, which is particularly important for organizations with strict compliance requirements.
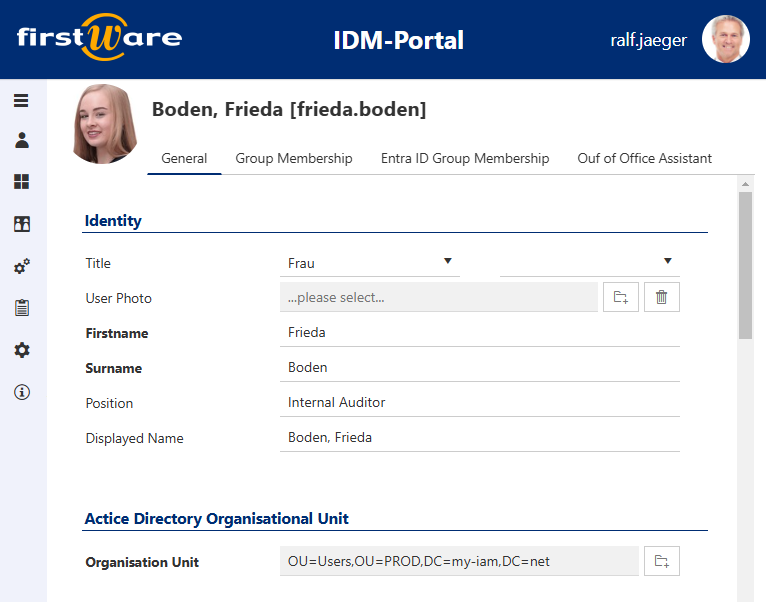
Onboarding in Entra ID
Onboarding in Entra ID is a central component of cloud-based identity and access management. The process begins with
- the creation of a new user account in the Entra Admin Center or
- by synchronizing from an on-premises Active Directory.
The user is then assigned the required licenses and access rights to cloud resources. Entra ID offers advanced features such as multi-factor authentication (MFA) and conditional access policies. These features ensure that only authorized users can access resources under certain conditions
This onboarding process is particularly suitable for companies with a “cloud-first” strategy, where most applications and data are managed in the cloud. Entra ID offers significant advantages for companies with distributed locations. It is beneficial for remote workers who depend on seamless access to cloud resources.
A common problem is the complexity of managing permissions and roles in large environments. It can be difficult to ensure that users have only the minimum necessary rights. This is especially challenging when managing roles in different cloud services and applications.. In addition, synchronization problems can occur between Entra ID and the on-premises AD. This can lead to inconsistent user profiles or outdated access rights.
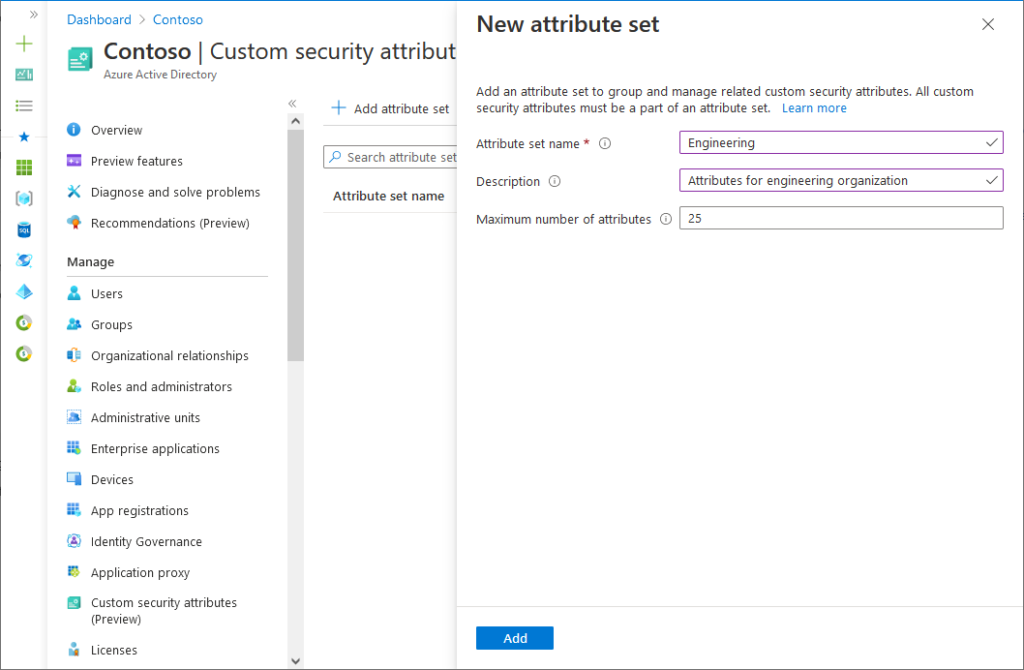
Creating new attribute sets in the Entra ID admin center
The FirstWare IDM-Portal also offers a comprehensive solution here by providing a central platform for managing user identities and permissions in Entra ID. The portal automates the process of assigning and removing rights and ensures that all changes are synchronized in real time. In addition, the IDM-Portal enables security policies and compliance requirements to be applied in both Entra ID and all connected systems. It significantly simplifies administration and reduces the risk of security breaches. This makes it particularly valuable for organizations that want to securely and efficiently manage their cloud environment.
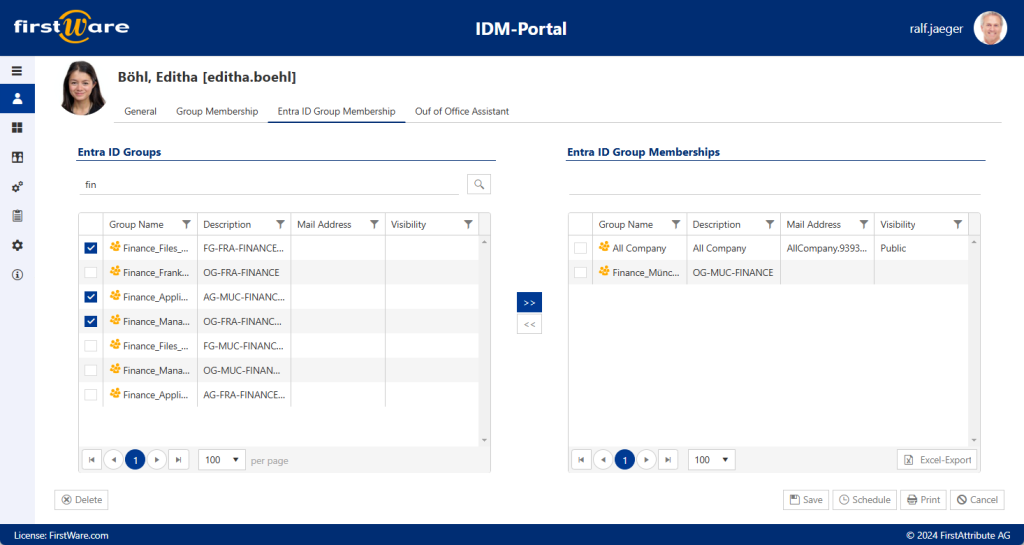
Onboarding in third-party systems
Conclusion
Hybrid onboarding in Entra ID, Microsoft 365 and Active Directory is a complex but crucial task in modern IT infrastructures. It seamlessly and securely integrates users into both on-premises and cloud-based systems. Administrators must overcome numerous challenges, from synchronizing AD and Entra ID to consistently managing access rights and ensuring compliance.
The FirstWare IDM-Portal from FirstAttribute proves to be a user-friendly and practical solution in this context. It enables centralized, automated management of onboarding in both environments, significantly reducing the typical sources of error and security risks. Through seamless integration and synchronization of identities in AD and Entra ID, the IDM portal ensures consistent and secure user management.
FirstAttribute AG – Identity Management & IAM Cloud Services
We would be happy to present our services and solutions to you. Get in touch and find out how we can help you.






Leave a Reply
<p>Your email is safe with us.<br/>Information about our <a href="https://activedirectoryfaq.com/contact-us/">data protection policies</a></p>