For the implementation of a zero trust strategy, conditional access in Entra ID is an important basis for protection against cyberattacks. This article highlights the key points. Conditional Access in Microsoft Entra ID is a central component of the Zero Trust security model, designed to precisely control access to company resources and minimize risks. It plays a critical role in securing access to sensitive data and applications.
Index
Challenges in the Modern IT Environment
The rise of remote work and cloud environments has expanded the attack surface for companies. Employees often access corporate resources from non-optimized networks or devices, increasing vulnerability. Access from insecure geographic locations also poses risks. Attackers exploit these weaknesses to gain access to sensitive data. This is where the Zero Trust model comes into play, and Conditional Access is a key technology in securing logins to Entra ID.
The Zero Trust model assumes that no network traffic or access request is inherently trustworthy. Every access is verified, regardless of whether it originates from within or outside the network. Three main principles define this model:
- Explicit verification: Every access is thoroughly checked, for example, through multi-factor authentication (MFA) or device certifications.
- Least privilege access: Users and devices receive only the minimal rights necessary to perform their tasks.
- Assumption of a breach: Every access request is initially treated as a potential threat until proven otherwise.
Conditional Access as a Core Component
Conditional Access in Entra ID allows companies to create dynamic policies that grant or deny access based on various conditions. A range of signals are considered, such as the user’s location, the device being used to access resources, or user behavior in managing resources and logins. Typical examples of signals and conditions used in Conditional Access include:
- User and location information: It can be checked where or from which network the access is coming from.
- Device status: Devices must meet certain security requirements to gain access, such as compliance status or hybrid join in Azure AD.
- Application access: Depending on the application, access may be restricted with additional security measures such as MFA.
Conditional Access allows for enforcing differentiated policies. For example, users with high risk (based on anomalies in login behavior) may require MFA, while no additional authentication step is needed for trusted devices or locations. Similarly, access to company resources can be limited to trusted locations and devices.
Using Microsoft Entra ID Governance
Microsoft Entra ID Governance is a solution for managing and controlling identities and access rights in an organization.
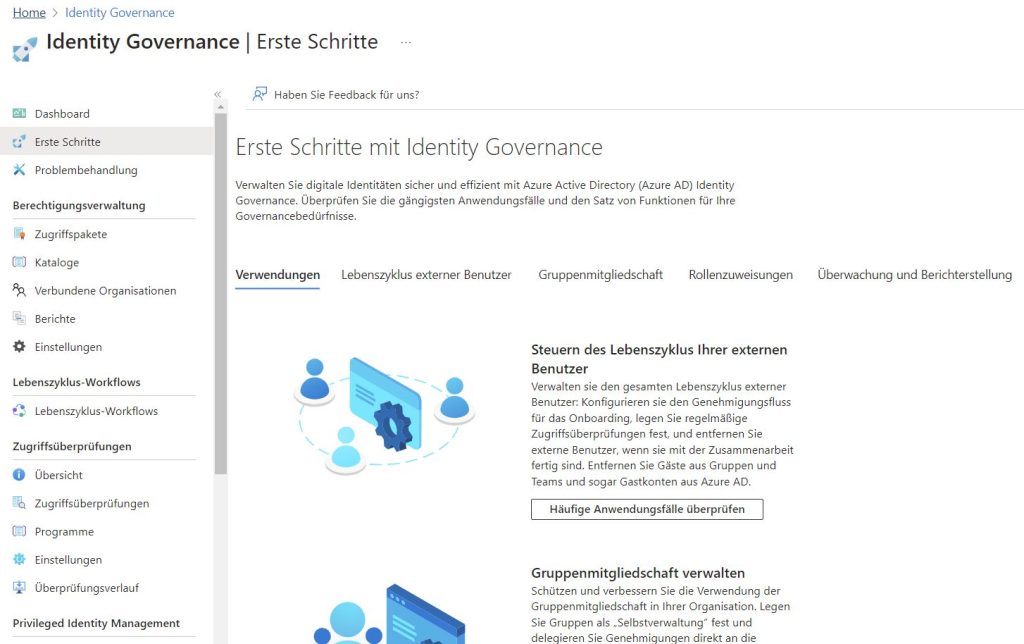
Microsoft Entra ID Governance offers comprehensive features for managing and controlling identities and access rights in companies. The solution helps organizations manage the entire identity lifecycle, particularly in relation to Azure and Entra ID. Processes for creating, updating, and deleting user accounts can be automated, significantly improving management efficiency and security. This article explores the wide-ranging applications and benefits of the solution, with a focus on effective management of permissions and group memberships.
A core element of Entra ID Governance is the enforcement of policies that ensure only authorized individuals have access to specific resources. This is achieved through role-based access controls (RBAC) or Conditional Access. Permissions are assigned according to users’ tasks and responsibilities, complemented by monitoring and reporting functions that enable continuous oversight of access activities. Companies can quickly identify suspicious access patterns and respond accordingly. All configurations are handled in the Entra Admin Center.
License Options and Advanced Features
Microsoft Entra ID Governance is available in various license models, including a free version as well as the paid P1 and P2 licenses. The basic version includes essential features such as object creation and basic security measures. The P1 license expands on this with additional features like Conditional Access management and continuous access reviews. For many companies, this is the ideal entry point, as it also includes password protection policies and self-service password reset options.
The P2 license builds on these features, offering advanced options such as identity protection for users and sessions, as well as advanced governance functions like Privileged Identity Management (PIM) and access reviews. These enhanced features allow companies to strictly control access to critical resources and conduct regular reviews of access rights. All functions can be managed through the Entra Admin Center. Microsoft provides an overview of the license differences on a dedicated website.
Lifecycle Workflows and Machine Learning
With Entra ID Governance, companies also have access to features like Lifecycle Workflows, which automate onboarding and offboarding processes. These workflows include, among other things, the provision of temporary access passes and notifications to responsible parties at specific times. Additionally, the integration of machine learning in access reviews allows for the identification of unnecessary permissions. These technologies optimize access rights and reduce security risks.
Another feature of Entra ID Governance is the use of verified identities. These allow for targeted management of access rights for internal and external users based on verifiable identity credentials. Through the sponsor concept, responsible parties for external users can be designated to manage and approve their access.
Practical Application
Challenges in Managing Resource Access
In practice, Entra ID Governance offers numerous functions to effectively manage access to resources. An example is the management of group memberships. In many companies, administrators not only manage who is in a group but also decide which members should have access to certain resources. In complex environments, this can be challenging, especially if it is unclear who should belong to a group. Entra ID Governance can assist by enabling administrators to create access packages that bundle access to multiple resources.
Access Packages in Entra ID
Access packages in Entra ID provide an efficient way to manage access to resources such as groups, applications, and SharePoint sites.
Administrators can:
- Set detailed policies to ensure that only authorized users gain access.
- Establish approval processes to monitor and control access.
- Conduct regular reviews to ensure that permissions remain necessary.
Additionally, advanced features such as verified identities and sponsors enable more precise and secure access management.
Managing Access Packages
Microsoft Entra ID Governance provides numerous features to help organizations control and secure access to their resources. By clicking the “Create Access Package” button in the Identity Governance dashboard, you can open the page to create and manage such packages. Use “New Access Package” to create one.
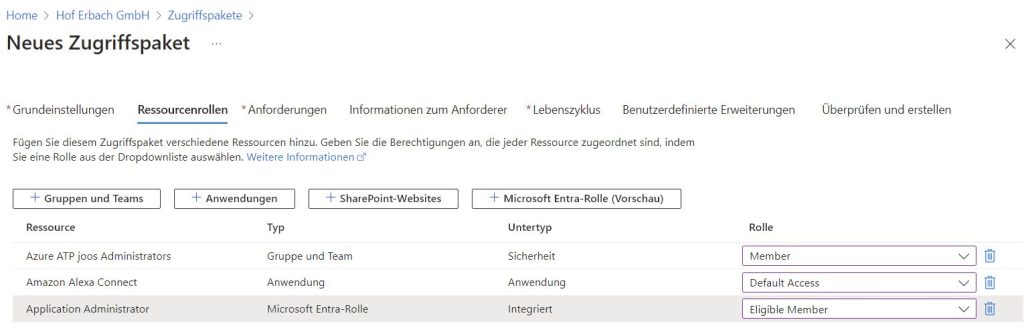
During the assistant’s process, you will set the name and select the catalog in which the access package will be managed, typically “General.” When assigning resource roles, you can specify which user role a user will receive when the access package is assigned to them, such as “Owner” or “Member.” It is also possible to select “No” for automatic assignment, meaning an administrator must manually assign the access package.
Another important aspect is the ability to control access rights through “Requests.” The approval process can be established by enabling “Approval.” You determine who acts as the “First Approver” and can set “Justification from the requester required,” meaning the user must provide a justification for their request. You can also ensure that requests do not go unanswered with “If no action is taken, forward to an alternative approver?”
Lifecycle and Access Control
Regarding the lifecycle of permissions, the “Lifecycle” feature allows you to specify when the rights defined in the access package will expire. “Access Control” also enables regular checks to see if a user still needs their access rights. Further customizations can be made through “Custom Extensions.”
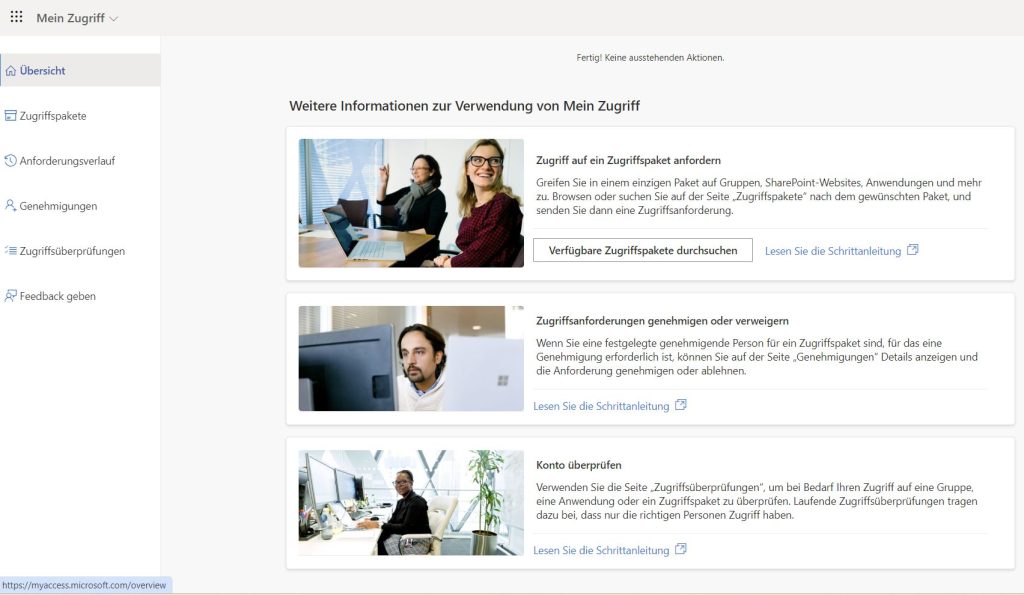
Package and request management is done through the “myaccess.microsoft.com” website. Here, users can access the relevant packages and submit access requests via the “Request” button.
Conditional Access in Entra ID
Entra ID Premium P2 and Enhanced Security Features
Companies opting for Entra ID Premium P2 gain access to additional security features that work optimally with Entra ID Identity Governance alongside Identity Governance. The system automatically detects anomalies during login attempts, such as:
- new devices,
- IP addresses, or
- locations.
Additionally, Entra ID detects anomalies in token usage patterns, such as
- unusually old tokens, or
- tokens used in an unexpected order.
Conditional Access and Policy Management
Conditional Access is available in Entra ID Protection under “Protection -> Security Center -> Conditional Access.” Here, policies can be created to govern user sign-ins. At this stage, the policy can also reference the results of the user risk policy and the sign-in risk policy. However, these two policies should no longer be used. It is better to rely directly on Conditional Access.
After creating a new policy, you first select whether it should apply to all users or only to specific user accounts. It is sensible at this point not to include the break-glass account. When creating a policy
- for Conditional Access, it can also be specified,
- which target resources the policy should apply to.
It is reasonable at this point to include all apps, essentially all resources available in Azure and Microsoft 365. Within the policy, it can also be specified what conditions must be met for a user to have to authenticate with MFA. Here, it is sensible to select the desired risk level under “User risk.”
In the user risk policy, the recognized risk is defined. This can be “High,” “Medium and higher,” or “Low and higher.” The risk level assigned to a user depends on their sign-in conditions, which are defined through conditional access, for example. Thus, when signing in, a user receives a user risk assignment. In the user risk policy, it can then be defined what access users with each risk level should have. Here, access can be blocked, allowed, or password changes can be enforced.
Conditional Access and Identity Protection
With the P2 license, companies also gain access to Entra ID Identity Protection and Conditional Access. These security features enable risk-based management of Azure resources. Entra ID uses machine learning and expert-developed security mechanisms to detect and respond to sign-in risks. The rules for conditional access can be configured to require additional security measures, such as Multi-Factor Authentication (MFA), when an increased risk is detected.
FirstAttribute AG – Identity Management & IAM Cloud Services
We would be happy to present our services and solutions to you. Get in touch and find out how we can help you.








Leave a Reply
<p>Your email is safe with us.<br/>Information about our <a href="https://activedirectoryfaq.com/contact-us/">data protection policies</a></p>