Extension attributes in Entra ID offer more flexibility and customization options. Custom attributes allow you to store additional information to more effectively manage user accounts and personalize applications. Learn how extension attributes and schema extensions differ, including their use cases and limitations.
Index
What are extension attributes in Entra ID and what types are there?
In Entra ID (formerly Azure AD) there are two main categories for the implementation of custom attributes: Extension attributes and schema extensions. This distinction enables flexible customization of identity objects such as user accounts and groups to meet specific requirements of organizations that go beyond the standard attributes.
Extension attributes
Extension attributes provide a simple and directly available method of storing additional information in identity objects. Entra ID contains a number of ready-made extension attributes (for example, extensionAttribute1 to extensionAttribute15) that are available without prior configuration. These attributes are particularly useful as they enable quick implementation without the need for complex adjustments to the schema. The values of these attributes can be set both via the Entra ID Admin Center and programmatically via the Microsoft Graph API, which enables a high degree of flexibility in administration.
Schema extensions
In addition to the standard extension attributes, there are schema extensions that allow deeper customization of the Entra ID schema. In contrast to the predefined extension attributes, schema extensions allow the addition of completely user-defined attributes to various identity objects. This flexibility makes it possible to support more complex requirements and scenarios. In these cases, specific data models are required that go beyond the standard attributes and the simple extension attributes. However, the use of schema extensions requires careful planning and implementation as they directly change the underlying schema of Entra ID.
In summary, extension attributes and schema extensions in Entra ID provide two powerful mechanisms for extending and personalizing identity management within an organization. While extension attributes provide a simple and out-of-the-box solution for additional user data, schema extensions allow deep customization of the directory schema for more complex requirements. The choice between these options depends on the specific needs and scenarios of an organization.
Why are Entra ID extension attributes needed?
The custom attributes can be used to store user addresses, for example in the home office, or security features and information that is important for user assignment. Finally, the attributes make the user accounts more flexible and easier to filter.
Attribute extensions can also be used to filter dynamic groups. The filters can be set up on the basis of the company-specific Entra ID extension attributes and can therefore be used flexibly.
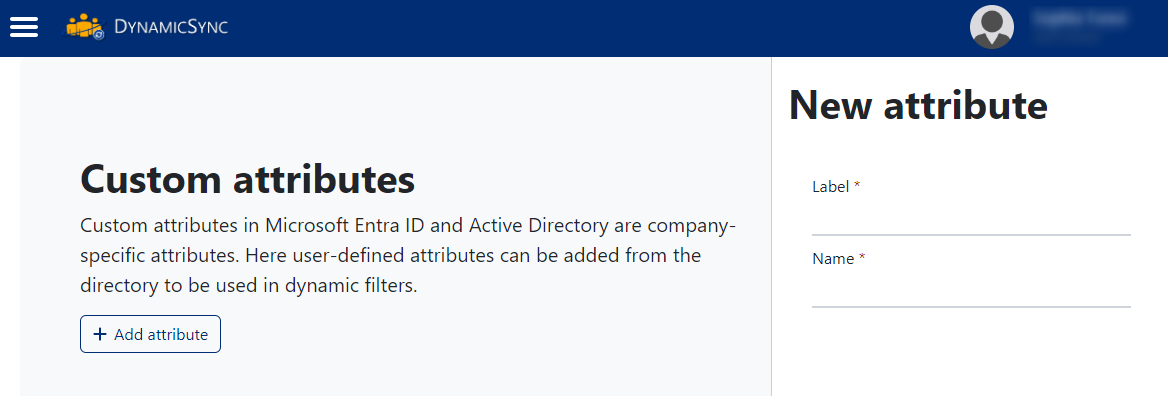
Create rules for dynamic memberships in Entra ID
If additional solutions such as my-IAM DynamicSync are used in this context, the custom attributes are quickly and easily added as filters in the DynamicSync configurator. These attributes are then permanently available as a dynamic filter.
The attributes also play an important role in the synchronization of local AD environments with Entra ID.
Extend Entra ID directory schema with AD attributes
The directory schema in Entra ID can be extended with your own attributes from a local Active Directory. This functionality enables organizations to store additional information about user accounts that goes beyond the standard attributes. This can be useful, for example, for managing employee IDs, departmental affiliations that are not directly mapped in the standard attribute set, or for specific use cases such as access control and personalization of applications.
This makes it possible to bring your own attributes from the AD to the cloud via user synchronization and use them there. This offers various advantages, for example:
- more effective filtering of users and groups,
- more flexible assignment of authorizations and roles and
- a company-specific assignment of users from Entra ID to your own applications.
With Microsoft Entra Connect, companies can continue to manage user-defined attributes for industry software locally and use them in the cloud at the same time.
What are the advantages of custom attributes?
Let’s assume a company wants to get a quick overview of all employees working on a specific project who also have a specific security clearance. For this purpose, user-defined attributes such as “ProjectID” and “SecurityClearanceLevel” could be created and assigned to the user profiles. In the same way, it is also possible to create attributes for assignment to dynamic groups.
Administrators can define a query using dynamic filter queries in the administration console or via the API. This query only lists the users whose ProjectID corresponds to a certain project and whose SecurityClearanceLevel exceeds a certain value.
Microsoft has made custom attributes available as an option in Entra ID, but has made administration quite complicated. Companies that want to use their own filters, for example to control membership in dynamic groups, do not have an easy time with the custom attributes. By default, the filters have to be added individually for each group. With a large number of groups, this is very cumbersome and time-consuming.
By using solutions such as my-IAM DynamicSync, this problem can be solved quickly, as the assignment of attributes can be solved directly in a clear interface. In addition, the attributes are permanently available in the filter for all groups. Manual assignment of attributes for each individual group, as in Entra ID, is therefore no longer necessary. This makes the use of custom attributes even more effective, as they can be used quickly and clearly.
Where can extension attributes not be used?
In standardized authentication and authorization processes we often cannot use custom attributes directly. Authentication protocols such as OAuth2 or OpenID Connect require specific customizations or extensions to add custom attributes to the standardized claim sets.
The integrated security and compliance functions of Entra ID, such as Conditional Access or Identity Protection, do not support the use of user-defined attributes. These services use Entra ID’s default attributes and identity data. In most cases, user-defined attributes cannot be referenced or evaluated directly within these security mechanisms.
When users use third-party software and services that allow integration with Entra ID, they often cannot use custom attributes. Unless the integration has been specifically designed to support them.
Many applications are primarily configured to handle standard attributes. They do not offer native support for importing or processing user-defined attributes.
You can use conditional access to force access requests if certain conditions are met.
For synchronization with other identity providers or directory services such as Active Directory on-premises, the use of custom attributes can be challenging. While Entra ID Connect can synchronize certain custom attributes between Entra ID and the local Active Directory, this requires additional configuration and is not suitable for all custom attributes or scenarios.
Custom attributes are not always displayed in the user interface of standard Entra services and management tools or cannot be edited. In such cases, administrators may need to use advanced tools or the Microsoft Graph API to work with custom attributes.
These limitations do not mean that custom attributes in Entra ID are not useful, but that organizations need to think through their use carefully. They may need to be supported by additional development or configuration so that they can be effectively integrated into an organization’s existing processes and systems.
Entra ID extension attributes with DynamicSync

With DynamicSync, my-IAM offers a cloud service that allows dynamic filters to be created and managed very flexibly in Entra ID. DynamicSync also supports user-defined attributes.
The improved configuration interface allows administrators to assign custom attributes and use them directly for the dynamic filters. This new feature ensures that attributes are permanently available once they have been defined. This offers a considerable advantage over the current handling in Entra ID.
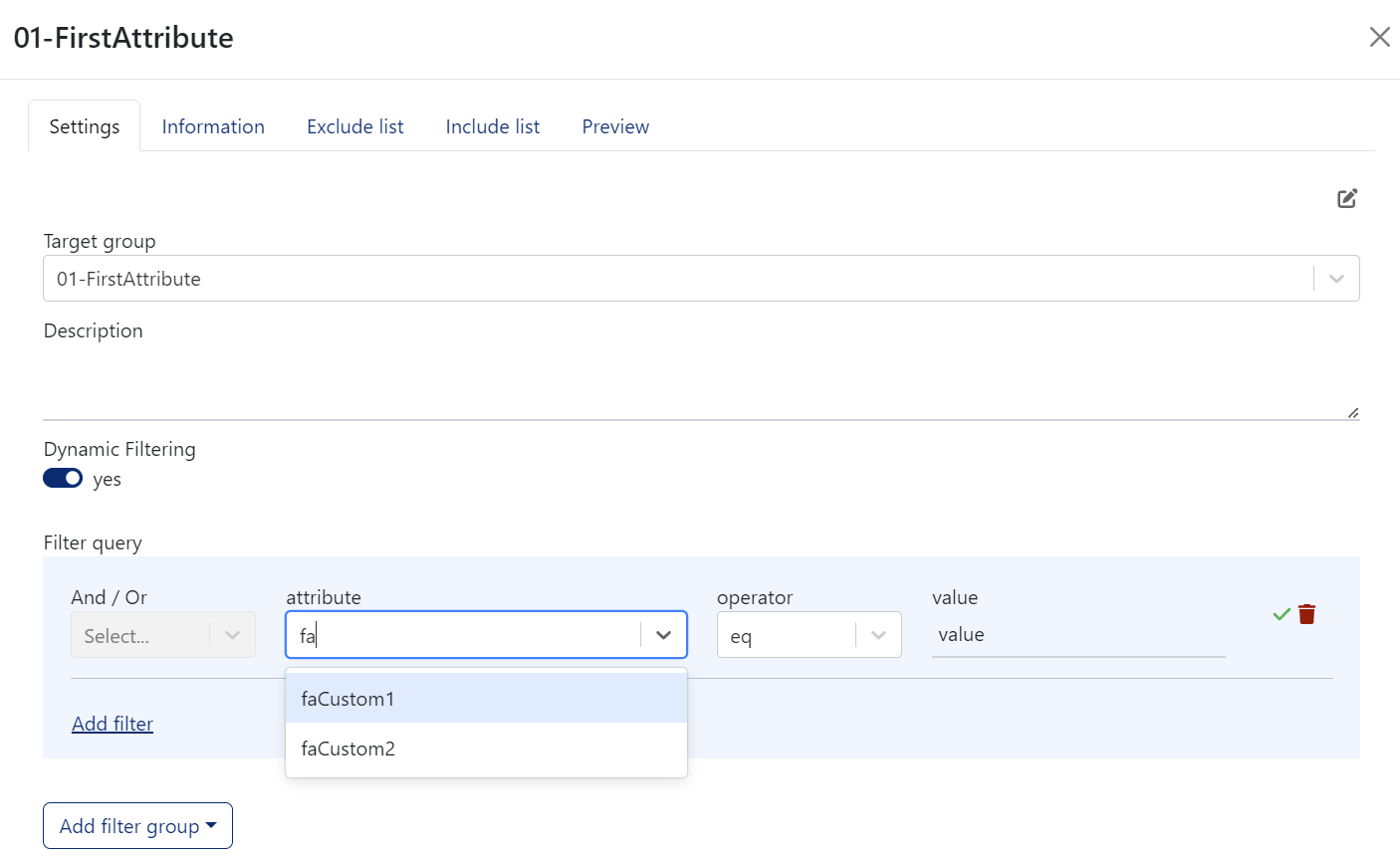
DynamicSync creates filter queries for dynamic group memberships in Entra ID: Select custom security attributes for dynamic filters
DynamicSync also enables the creation of up to 50 nested filters for dynamic groups. This supports granular and flexible group management, even in conjunction with dynamic groups.
DynamicSync opens up new possibilities for role management within Entra ID. In contrast to the limitations of Entra ID, DynamicSync enables the dynamic assignment of roles based on departmental affiliations or other criteria. For example, employees can automatically receive the appropriate access rights to view certain areas within a cloud environment.
Neither a local installation nor an Entra ID P1 subscription is required to use DynamicSync. The solution can synchronize groups in Entra ID and add group members via dynamic filters. DynamicSync is therefore a comprehensive solution for managing groups in Entra ID.
FirstAttribute AG – Identity Management & IAM Cloud Services
We would be happy to present our services and solutions to you. Get in touch and find out how we can help you.









Leave a Reply
<p>Your email is safe with us.<br/>Information about our <a href="https://activedirectoryfaq.com/contact-us/">data protection policies</a></p>