Azure AD Security Attributes are key-value pairs that can be custom created in Azure AD. This allows users to be assigned enterprise applications or various Azure resources (for example, specific values such as cost center, project affiliation, or personnel number) as a custom attribute. These attributes are available in full subscription for a variety of resources. They require an Azure AD Premium P1 or P2 subscription to be deployed. Attribute management takes place in the Azure Active Directory admin center.
Index
Roles for rights management in Azure AD
In addition, it is possible to control which user accounts are allowed to maintain and read these attributes. For this purpose, Microsoft has integrated various roles in Azure AD that have different rights for managing the attributes. The roles allow specific control over who is allowed to create, assign or read the attributes. Attribute governance controls access to sensitive information without restricting its usefulness. Boolean values, integers or strings are available as data types. It is also possible to store multiple values. In addition, the definition of predefined values is possible.
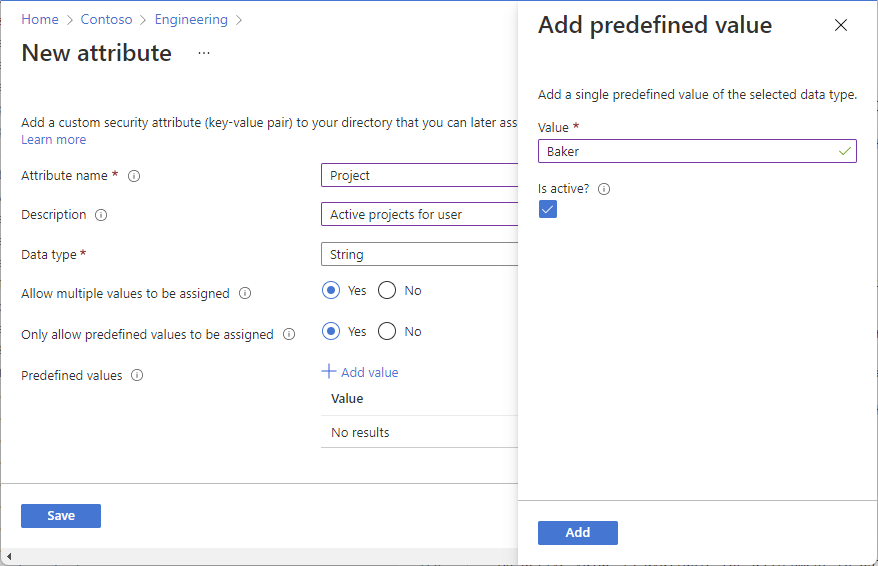
Azure AD synchronization: Assigning security attributes to users from Active Directory
It is possible to assign security attributes to users that have been synchronized from Active Directory to Azure AD. In this case, care should be taken to ensure that the other attributes in Active Directory are correctly maintained so that cooperation with Azure Active Directory custom security attributes works in an optimal way. Microsoft provides various options for this, which we have already covered in various articles, for example in “Azure AD Connect and Azure AD Connect Cloud Sync“.
Solutions such as FirstAttribute’s FirstWare IDM Portal help properly maintain attributes in Active Directory so that synchronized accounts can be enhanced with security attributes. The IDM-Portal enables comprehensive automation of all identity management tasks and delegation of tasks to HR or elsewhere in the organization. The same users can subsequently be authorized to control security attributes in such a scenario. The IDM-Portal does not rely on proprietary technologies, but uses functions that Microsoft has integrated in Windows, Active Directory, Azure and Microsoft 365/Office 365.
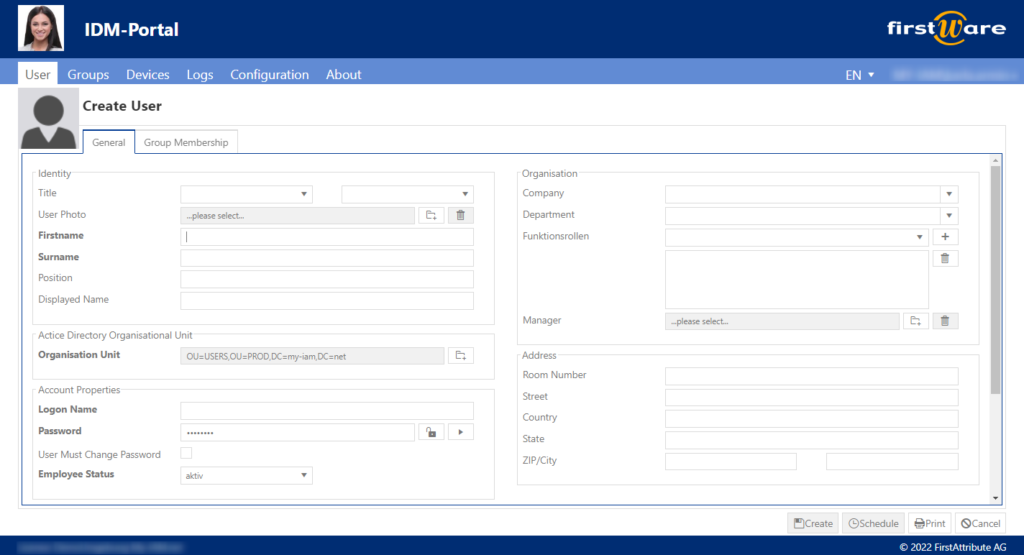
Only properly maintained attributes in Active Directory result in correctly synchronized data in Azure AD. If these AD users subsequently receive custom security attributes in Azure AD, all other attributes also play a role. Based on the collected attributes, users can be assigned comprehensive rights. Filters can also be set in this way so that they function properly. The creation of groups with attributes works in the same way. The correct maintenance of all attributes is important.
Add-on tool further enhances the utility of Azure Active Directory custom security attributes
In parallel, the cloud-based tool DynamicSync can handle synchronization of groups in Azure AD. When using DynamicSync, administrators maintain groups and permissions in on-premises Active Directory forests. They then synchronize the groups to the cloud and further edit them with DynamicSync. The tool is also capable of synchronizing security attributes. In turn, the synchronized accounts can also receive additional security attributes in Azure AD, which are added in addition to the attributes from AD, for example, to control groups from Active Directory to Azure AD.
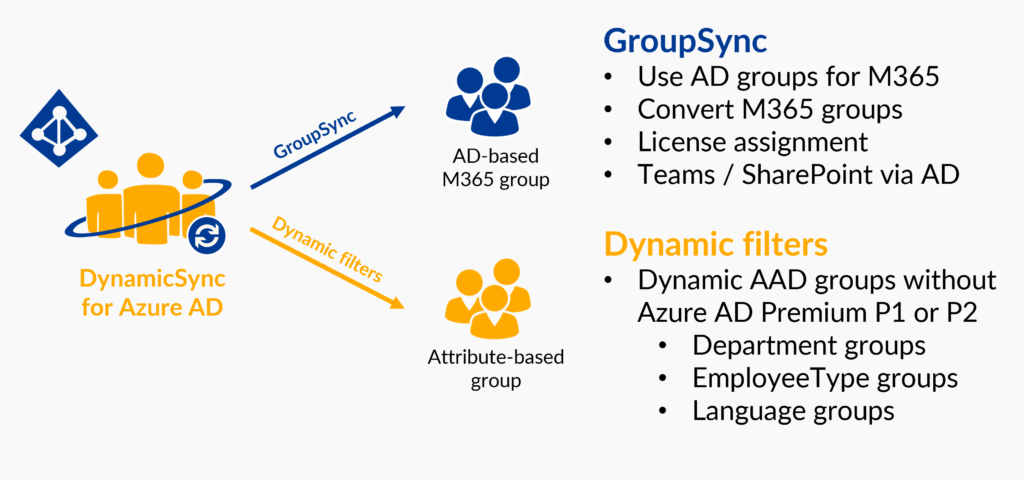
Together with the IDM-Portal, this results in a solution with which accounts in Active Directory and Azure AD are in harmony, synchronized with each other, and at the same time can also be combined into groups and thus teams:
- Dynamic groups can be maintained in Active Directory and Azure AD in a fully automated way
- Synchronization of Azure AD groups into new M365 groups, for example for Microsoft Teams
- Adding and removing members to the synchronized groups
- Creating attribute-based groups with dynamic filters, also based on Azure Active Directory custom security attributes
The group can be maintained in the local Active Directory either by conventional means or with additional tools such as the FirstWare IDM-Portal. This makes it relatively easy to synchronize complete authorization structures to the cloud and use them in Microsoft Azure and Microsoft 365. These optimally maintained user accounts can now be further enhanced with Azure Active Directory custom security attributes in a highly effective manner.
More security and transparency in Azure AD with Azure Active Directory custom security attributes
Azure Active Directory custom security attributes also allow sensitive data to be stored in this location, for example, hourly rates, hire dates, or other information. Global admins are not initially allowed to read attributes or maintain attributes. These admins are only allowed to assign permissions to whoever has those permissions, including themselves, of course. This shows that Azure Active Directory custom security attributes have great relevance to security and privacy. The right to read or edit them must be assigned explicitly.
These attributes provide the ability to store information about users and other resources in Azure while specifying who should have access. At the same time, internal systems in Azure can use this data, for example, to build dynamic groups in which only users who have certain attributes should be members. Azure Active Directory custom security attributes are also useful for filtering enterprise applications. This allows responsible parties to filter all enterprise applications based on different attributes and improve visibility. However, the attributes can do much more.
Use Attribute Based Access Control (ABAC) with Role Based Access Control (RBAC)
The user-defined attributes can then be assigned to user accounts in Azure AD and thus also used as objects for dynamic groups. These groups can be created based on attributes assigned to users. These can also be Azure Active Directory custom security attributes. These attributes can also be used when assigning rights in Active Directory via Azure role assignments.
In this area, the new security attributes work together with attribute-based access control (ABAC) in Azure. ABAC uses role-based access control (RBAC). This allows rights to be assigned to users with specific attributes in the user account. ABAC provides very granular tuning that RBAC is not capable of on its own. Microsoft describes how to use ABAC on the page “Introducing Attribute Based Access Control (ABAC) in Azure“.
How does using ABAC with Azure Active Directory custom security attributes work?
First, the Active Directory custom security attributes are created in Azure AD so that they are generally available in Azure AD first. The first step is to create an attribute set in the Azure Active Directory admin center, where different attributes can be collected. As long as it is a preview feature, it is not available in all subscriptions. The feature can be found at “Custom security attributes” directly after selecting “Azure Active Directory” in the Azure Active Directory admin center. New sets can be created here.
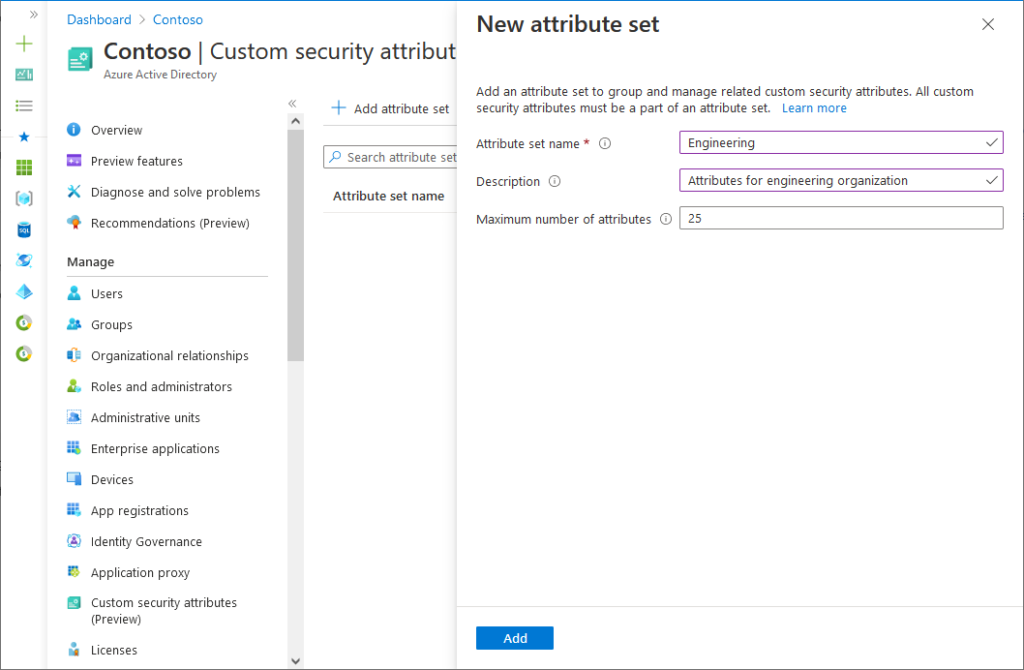
An example of this is “Engineering”. In this set, again, the various attributes that are required for “Engineering” are grouped together. Other sets can also be created in the same way, for example for different project groups. Microsoft shows how to do this on the page “Introducing Azure AD custom security attributes” and “What are custom security attributes in Azure AD?“
Once the attribute sets and their associated attributes are created, they can be assigned to enterprise applications or to users. In general, Azure Managed Identities can use the attributes from the individual sets. Once attributes are assigned, they can be used with the various filters in Azure. As an example, priorities can be assigned to different applications. Based on the custom attribute, applications can be filtered with a specific priority. Microsoft describes the procedure for this on the page “Add or deactivate custom security attributes in Azure AD“. The assignment of the attributes can again be found on the page “Assign or remove custom security attributes for a user”.
Managing Azure Active Directory custom security attributes in PowerShell
Azure Active Directory custom security attributes can also be managed in PowerShell. This allows the individual functions to be scripted. This is also useful when using solutions such as the FirstWare IDM-Portal from FirstAttribute. Here, for example, it is possible to execute PowerShell scripts when creating user accounts. The cmdlets for maintaining security attributes in Azure AD can also be maintained here. The individual sets can be displayed with the Get-AzureADMSAttributeSet cmdlet. A new set is created with “New-AzureADMSAttributeSet”, the sets can be updated with “Set-AzureADMSAttributeSet”, for example:
Set-AzureADMSAttributeSet -Id “Engineering” -Description “Attributes for cloud engineering team”
Set-AzureADMSAttributeSet -Id “Engineering” -MaxAttributesPerSet 20
All existing security attributes can be displayed with ” Get-AzureADMSCustomSecurityAttributeDefinition”, new attributes are created with “New-AzureADMSCustomSecurityAttributeDefinition”. Attributes can also be edited afterwards with “Set-AzureADMSCustomSecurityAttributeDefinition”. A list of all cmdlets can be found on the page “Add or deactivate custom security attributes in Azure AD“.
Dear readers of the ADFAQ blog. Thank you for your interest in our articles. Our experts write these articles to the best of their knowledge, but the world of IT changes quickly. As a rule, we do not update the written blogs or rather rarely. Therefore, we cannot guarantee that the content is always up to date. Here, you can find a link to the M365 Identity Management solution described in the article. Should you be interested in dynamic groups in Azure AD, DynamicSync is the tool for you.
FirstAttribute AG – Identity Management & IAM Cloud Services
We would be happy to present our services and solutions to you. Get in touch and find out how we can help you.








Leave a Reply
<p>Your email is safe with us.<br/>Information about our <a href="https://activedirectoryfaq.com/contact-us/">data protection policies</a></p>