Microsoft Teams supports all authentication options that are also offered by Microsoft 365/Office 365. This means that authentications for MS Teams can only take place in the cloud, i.e. via Azure Active Directory (AAD), but also in a hybrid way, together with Active Directory (AD). In hybrid deployments, it is possible to synchronise local AD accounts with Azure AD and use them together with Microsoft Teams. For many companies, local AD and its efficient maintenance play an important role even in times of comprehensive cloud migration.
Index
Microsoft Teams also works in Windows 10/11 without AD
If companies rely primarily on cloud solutions and want to authenticate various services in Microsoft 365 and Office 365, Azure AD is the preferred way. Azure AD is available even without on-premises synchronization and allows all users to be comprehensively authenticated via their accounts in Azure AD. With these accounts, users can log in to all Microsoft 365 services, including Teams. In parallel, it is also possible to log in to Azure AD on Windows 10/11 computers and also on Windows 365 in the cloud, thereby also accessing Microsoft Teams.
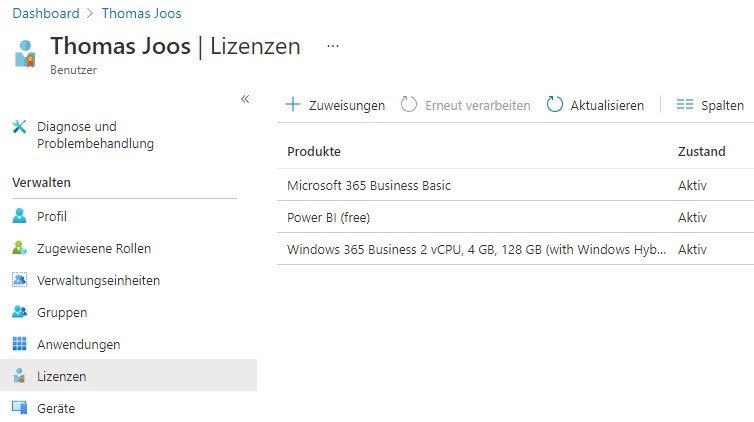
Manage user permissions and licenses in Azure AD
Microsoft Teams is already pre-installed on Microsoft’s cloud PC. Authentication is done by logging into Windows 365 or via the Teams app. The Windows desktop app can also be installed in Windows 365, just like in Windows 10/11 without cloud connection. After launching the app, the Teams client automatically logs the user in with the account they used to log in to Azure AD. This works without any problems even without AD.
Signing in to Microsoft Teams with an Azure AD account without an on-premises AD connection works on on-premises computers running Windows 10 and Windows 11. Signing in to Azure AD from an on-premises computer running Windows 11 does not require an on-premises AD to authenticate to cloud resources in Microsoft 365 with SSO. This works the same way in Windows 365. The cloud PC is based on Windows 10 or Windows 11 and provides the same capabilities.
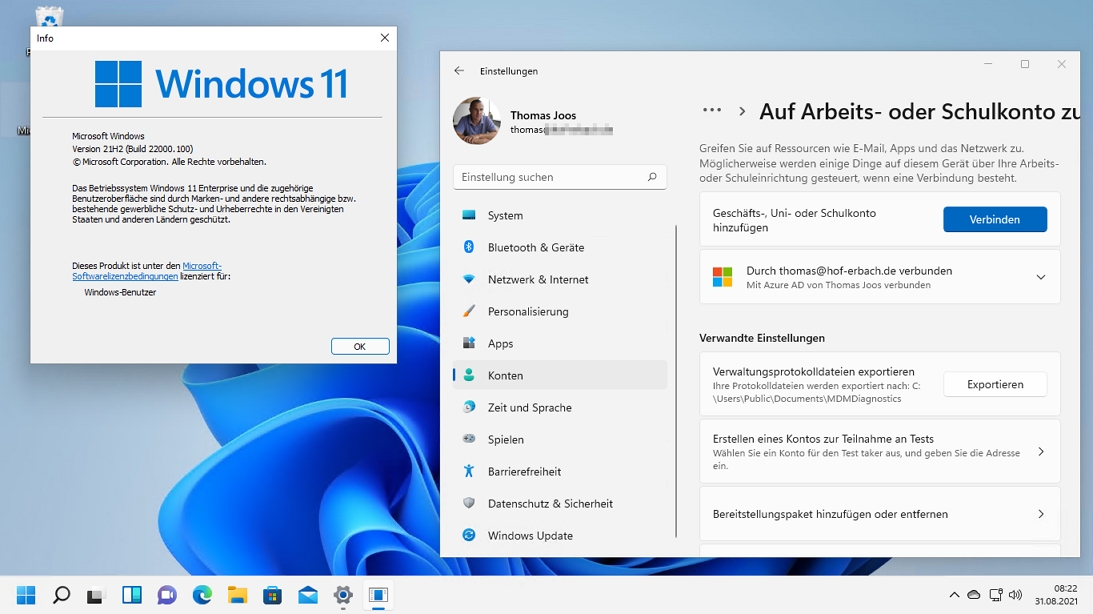 Windows 11 can also log on to Azure AD without requiring local AD.
Windows 11 can also log on to Azure AD without requiring local AD.Users therefore need an account in Azure AD to log on to the local computer. Of course, this account can also be transferred from AD to Azure AD via a synchronization, but this is not a prerequisite, it also works without AD. Using Windows 365 as an example, this also works with the Business edition, it is not necessary to use Windows 365 Enterprise.
Hybrid deployments with Microsoft Teams
Due to the flexibility of Microsoft Teams and the rest of the Microsoft 365 services as well as Azure AD, it is of course easily possible to combine local AD structures with Azure AD to form hybrid networks. Depending on the configuration, users in such environments can be authenticated either by Azure AD or by AD. In this case, directory synchronization between Azure AD and AD is necessary. This includes an optimally maintained Active Directory so that the data can be transferred without errors. We have discussed in detail how the transfer works in the article “Azure AD Connect and Azure AD Connect Cloud Sync“.
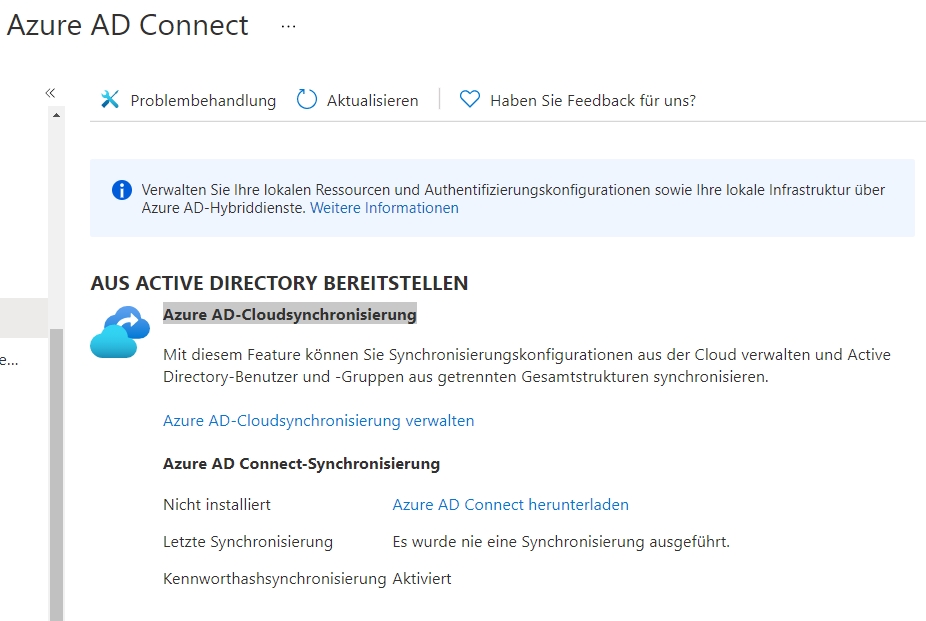
The article “Using single sign-on in Microsoft 365” (in German) also looks at how Microsoft 365 services, including Microsoft Teams, can be optimally operated in hybrid networks. To synchronize with Azure AD Connect, set up the synchronization, as can be read in the post “Install Azure AD Connect“.
Whether a user has access to Microsoft Teams in general can be adjusted in the Azure AD Admin Center for the respective user account under “Licenses” and then for the Microsoft 365 license that is linked in the subscription.
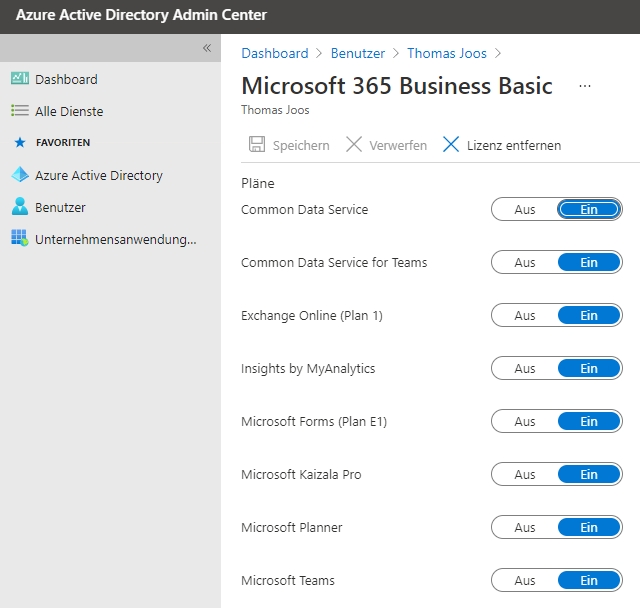
Control permissions in Microsoft Teams
As soon as the user accounts are available in Azure AD, they can also be used in Microsoft Teams. Initially, it does not matter for Teams whether the user accounts are created and authorized directly in Azure AD or whether the accounts come into the cloud via synchronization with an AD. Once the user account is available in Microsoft 365, a license for Teams can be assigned to the account in its settings. This can be done, for example, via the Microsoft 365 Admin Center (admin.microsoft.com) or automatically in an IAM solution with an interface to M365 applications, such as FirstWare IDM-Portal.
Within the Admin Center in Microsoft Teams, admins can also assign granular permissions to the environment, again based on the user accounts in Azure AD and thus in Microsoft 365. Again, it doesn’t matter how the accounts got to the cloud. So, in simple terms, this means that you can create user accounts in a structured way in your on-premises Active Directory and synchronize them with Azure AD.
You then use the accounts in Azure AD and Microsoft 365 in the same way as accounts you created directly in the cloud. In mixed environments, it is also possible to easily use accounts that exist exclusively in Azure AD, along with accounts that are synchronized between AD and Azure AD via tools. You set Microsoft Teams permissions in the Microsoft Teams Admin Center (admin.teams.microsoft.com).
Multi-level authentication with Teams and Microsoft 365
Security plays an even more important role for user account logins in the cloud than it does for on-premises logins. Even with synchronized accounts, multifactor authentication in Azure AD can be enabled for accounts in the cloud. Users could continue to work on their on-premises machines with their Active Directory account, but will need to log into Azure AD with multi-factor authentication once that is configured appropriately in the environment in Azure AD.
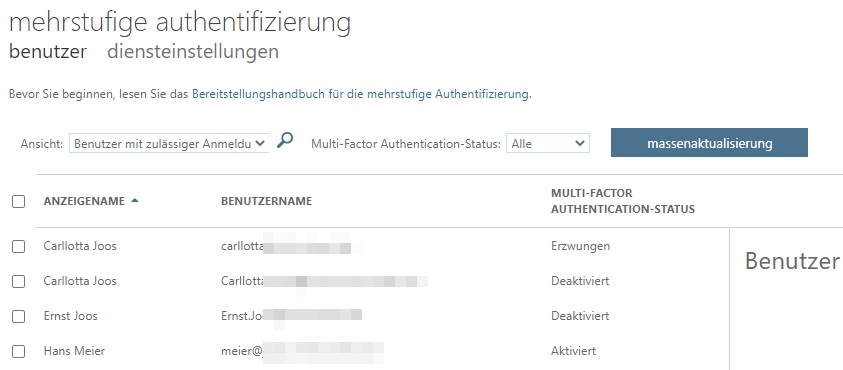
The second login can either be done via code, which Microsoft transmits via SMS or phone call, or via the free Microsoft Authenticator app. The advantage here is that users only have to confirm the logins without entering another code. In parallel, the app can also be used as a vault for credentials on the Internet, and of course for multifactor authentication for most other cloud services.
FirstAttribute AG – Identity Management & IAM Cloud Services
We would be happy to present our services and solutions to you. Get in touch and find out how we can help you.








Leave a Reply
<p>Your email is safe with us.<br/>Information about our <a href="https://activedirectoryfaq.com/contact-us/">data protection policies</a></p>