Do you need (again) to adjust your password generator after a policy change? The best way to avoid password generator adjustments after a policy change, is to generate passwords depending on the current Domain Password Policy. Here is how it works.
Index
Reading the password policies of a domain
First we want to read out the password policies of the domain. Via Server Manager > Tools there are two ways to find the policies:
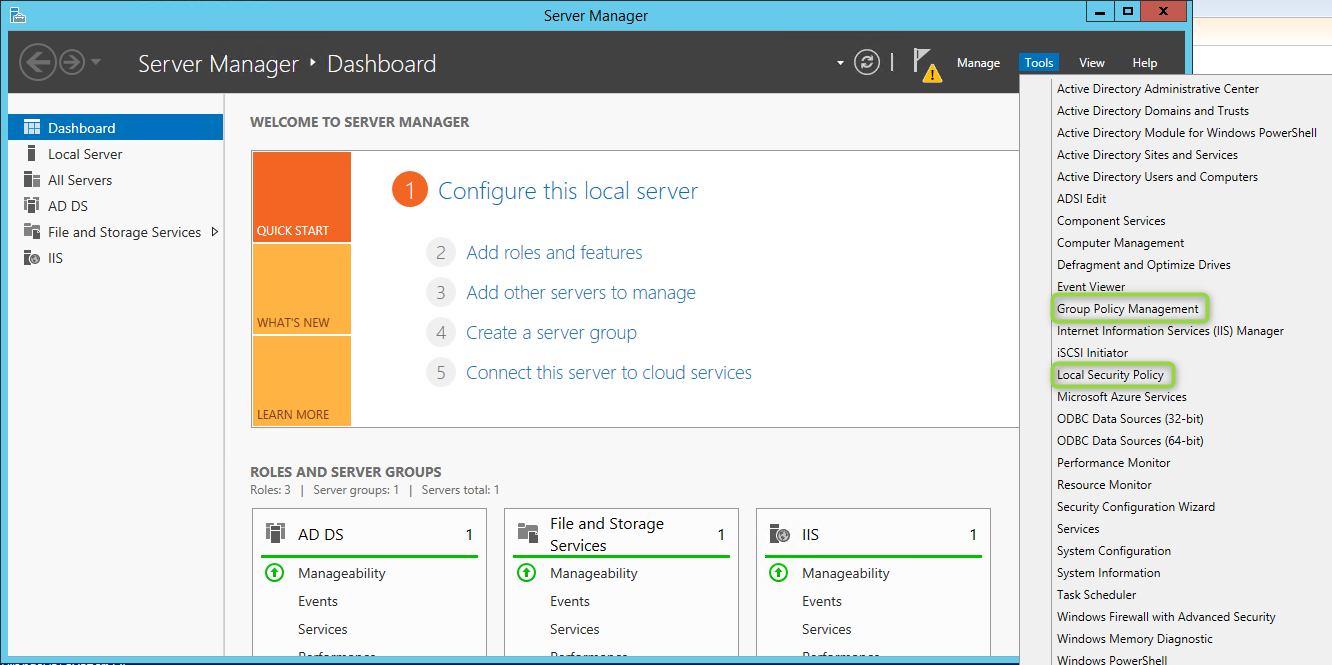
The Group Policy Management tool shows you all policies under the domain and default domain policy, including the password policy.
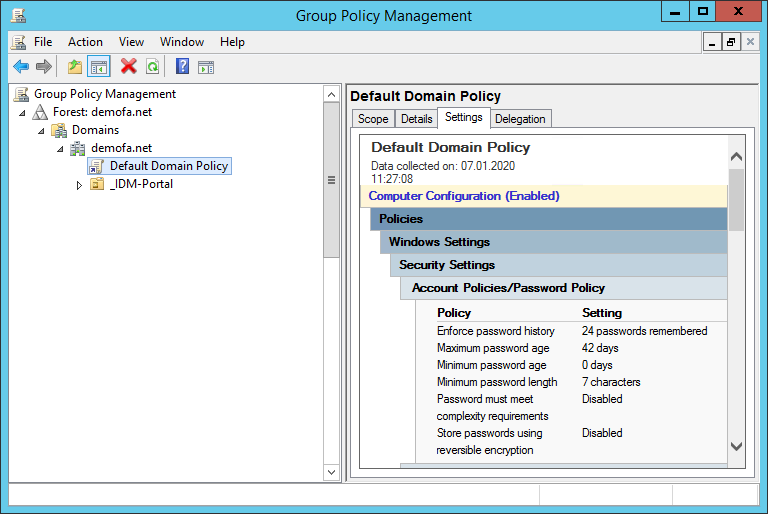
The password policies can also be displayed via “Local Security Policy”, but can also be changed with the appropriate permissions.
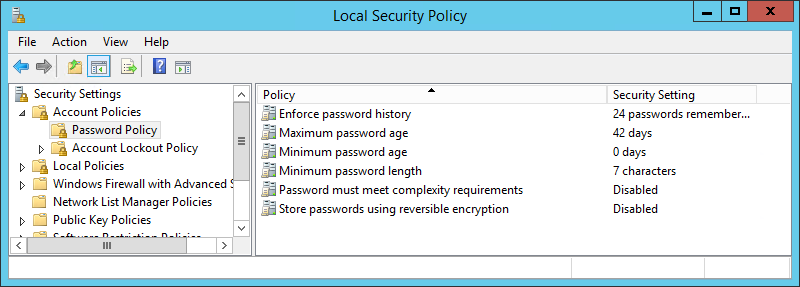
Password Policy Properties
The Password Policy consists of the following properties, which we can configure:
- PasswordHistoryCount
- MaxPasswordAge
- MinPasswordAge
- MinPasswordLength
- ComplexityEnabled
- ReversibleEncryptionEnabled
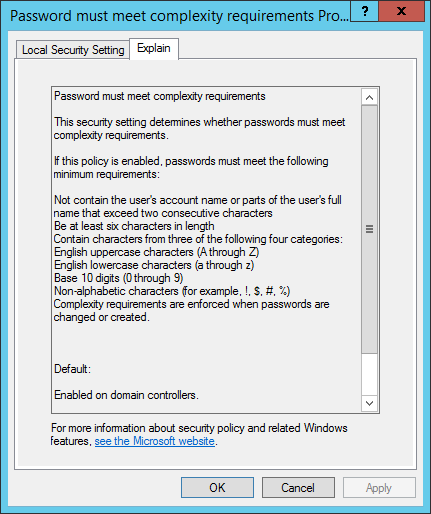
The ComplexityEnabled and MinPasswordLength properties are relevant. The Local Security Policy tool provides the following explanations:
ComplexityEnabled: if enabled,
- the passwords can not contain samAccountName or displayName
- passwords must be at least 6 characters long
- passwords must contain certain characters (at least one character from each of three of the four categories)
MinPasswordLength: Minimum length of passwords
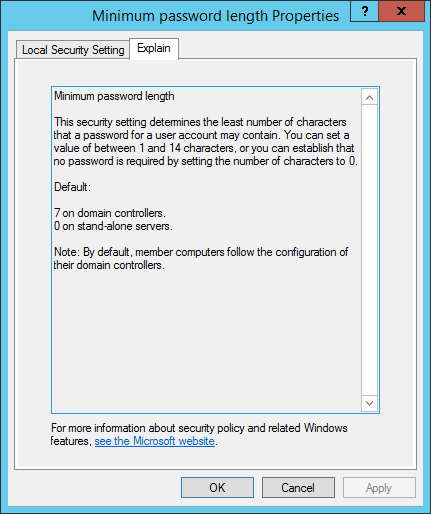
More information about here: https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/hh994560(v=ws.10)
The PasswordHistoryCount also plays a role, as when a new password is generated, it is not possible to check whether this password has been used before (within the specified number of old passwords).
PasswordHistoryCount: Number of used passwords to be stored in AD. They must not be reused by the user).
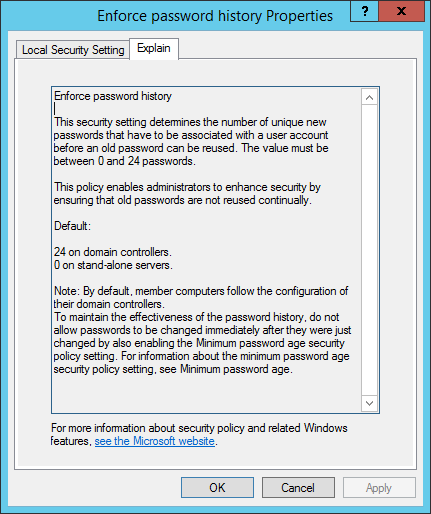
For more information, visit: https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/hh994571(v=ws.10)
Reading the Password Policy with PowerShell
The CmdLet Get-ADDefaultDomainPasswordPolicy can be used to easily read the domain’s password policy.
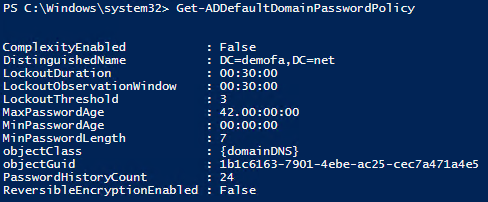
Other attributes such as LockoutDuration, LockoutObservationWindow and LockoutThreshold are listed here, which can be found in the Local Security Policy tool under Account Lockout Policy.
The CmdLet Set-ADDefaultDomainPasswordPolicy can be used to change the various properties using PowerShell.
First the relevant parameters are read out:
|
1 2 3 |
$policy = Get-ADDefaultDomainPasswordPolicy $complexity = $policy.ComplexityEnabled <span class="crayon-sy">$<span class="crayon-v">minLength</span> <span class="crayon-o">=</span> $<span class="crayon-v">policy</span>.<span class="crayon-i">MinPasswordLength</span> </span> |
Depending on the complexity set, the generation algorithms are applied, which can be customized as desired. We show here a possible example:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
if($complexity){ Write-Host("Komplexes Passwort wird generiert:") -ForegroundColor Yellow # Komplexe Passwort-Generierung $password = Get-RandomCharacters -length ($minLength - 3) -characters 'abcdefghijklmnopqrstuvwxyzß' $password += Get-RandomCharacters -length 1 -characters 'ABCDEFGHIJKLMNOPQRSTUVWXYZ' $password += Get-RandomCharacters -length 1 -characters '1234567890' $password += Get-RandomCharacters -length 1 -characters '!?:;,."§$%&amp;/|\()[]{}&lt;&gt;@#*-=+~^_' $password = Scramble-String $password }else{ Write-Host("Einfaches Passwort wird generiert:") -ForegroundColor Yellow # Einfach Passwort-Generierung $password = Get-RandomCharacters -length $minLength -characters 'abcdefghiklmnoprstuvwxyz' } |
![]()
![]()
As described in the article “PowerShell – Generate random password according to your own specifications” (currently only available in German), the following functions are used for this purpose:
|
1 2 3 4 5 6 7 8 9 10 11 12 |
function Get-RandomCharacters($length, $characters) { $random = 1..$length | ForEach-Object { Get-Random -Maximum $characters.length } $private:ofs="" return [String]$characters[$random] } function Scramble-String([string]$inputString){ $characterArray = $inputString.ToCharArray() $scrambledStringArray = $characterArray | Get-Random -Count $characterArray.Length $outputString = -join $scrambledStringArray return $outputString } |
Since we are dealing with a randomly generated password, we did not check whether the samAccountName and displayName of the user are included in the password. However, if the password is entered manually, a check is useful:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
$samAccountName = "user.test" $displayName = "Test User" if (($samAccountName) -and ($password -match $samAccountName)) { Write-Host("Passwort enthält samAccountName des Users") -ForegroundColor Red } if ($displayName) { $parts = $displayName.Split(",.-,_ #`t") foreach ($part in $parts) { if (($part) -and ($password -match $part)) { Write-Host("Passwort enthält Teile des displayName des Users") -ForegroundColor Red break } } } |
![]()
Since it is not possible to check the password history, the exceptions should be caught when setting the password for the user. In this way you can generate a new password if necessary.
|
1 2 3 4 5 6 7 8 9 10 11 |
try{ # …Code… } catch [Microsoft.ActiveDirectory.Management.ADPasswordComplexityException]{ $strException = $_.Exception.Message Write-Host("Passwort entsprich nicht den Richtlinien; Fehler: " + $strException) -ForegroundColor Red } catch{ $strException = $_.Exception.Message Write-Host("Fehler: " + $strException) -ForegroundColor Red } |
![]()
Avoid password generator adjustments – the complete script
Finally, here is the complete script to avoid password generator adjustments:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 |
function Get-RandomCharacters($length, $characters) { $random = 1..$length | ForEach-Object { Get-Random -Maximum $characters.length } $private:ofs="" return [String]$characters[$random] } function Scramble-String([string]$inputString){ $characterArray = $inputString.ToCharArray() $scrambledStringArray = $characterArray | Get-Random -Count $characterArray.Length $outputString = -join $scrambledStringArray return $outputString } $policy = Get-ADDefaultDomainPasswordPolicy $complexity = $policy.ComplexityEnabled $minLength = $policy.MinPasswordLength try{ if($complexity){ Write-Host("Komplexes Passwort wird generiert:") -ForegroundColor Yellow # Komplexe Passwort-Generierung $password = Get-RandomCharacters -length ($minLength - 3) -characters 'abcdefghijklmnopqrstuvwxyzß' $password += Get-RandomCharacters -length 1 -characters 'ABCDEFGHIJKLMNOPQRSTUVWXYZ' $password += Get-RandomCharacters -length 1 -characters '1234567890' <code> $password += Get-RandomCharacters -length 1</code> -characters '!?:;,."§$%&/|()[]{}<>@#*-=+~^_' <code> </code> <code>$password = Scramble-String $password }else{ Write-Host("Einfaches Passwort wird generiert:") -ForegroundColor Yellow # Einfach Passwort-Generierung $password = Get-RandomCharacters -length $minLength </code>-characters 'abcdefghiklmnoprstuvwxyz' } Set-ADAccountPassword -Identity $samAccountName -Reset -NewPassword (ConvertTo-SecureString -AsPlainText –String $password -Force) } catch [Microsoft.ActiveDirectory.Management.ADPasswordComplexityException]{ $strException = $_.Exception.Message Write-Host("Passwort entsprich nicht den Richtlinien; Fehler: " + $strException) -ForegroundColor Red } catch{ $strException = $_.Exception.Message Write-Host("Fehler: " + $strException) -ForegroundColor Red } |
Conclusion
In the article “PowerShell – Generate random password according to own specifications” (currently only available in German) we presented a way to create passwords with PowerShell. This script can also be used in our identity & access management solution FirstWare IDM-Portal, as described. If the password policy in the company changes now, this script does not necessarily have to be adapted if the domain’s password policy is observed from the outset. The passwords will then always be generated based on the current policy.
For non-IT employees who are administrating, this means no change. For example, if the HR department creates a new user in AD, the modified password generator script is automatically loaded.
FirstAttribute AG – Identity Management & IAM Cloud Services
We would be happy to present our services and solutions to you. Get in touch and find out how we can help you.









Leave a Reply
<p>Your email is safe with us.<br/>Information about our <a href="https://activedirectoryfaq.com/contact-us/">data protection policies</a></p>