After a Schema Update for Windows 2008 R2 on Windows 2012 R2 we had a problem with an older application on Windows 7. But the domain functioning level was unchanged.
The application checked with Kerberos whether a user has a certain group membership. Unfortunately, we couldn’t see the source code and thus didn’t know what the application actually did.
Index
Schema Update: New well-known SIDs
Usually there are no problems after Schema Updates. But if they occur it’s hard to find the reason. Luckily this problem turned out to be a reproducible one. The reason it occured were some new Well-known SIDs added during the Schema Update.
Those well-known SIDs are:
- S-1-18-1
- S-1-18-2
These SIDs are written in tokens in order to differentiate between a client connecting via authentification centre with client credentials (S-1-18-1) or with some service (S-1-18-2).
More information about well-known SID: Microsoft MSDN – Well-Known SIDs
Problem with Windows 2008 R2 and Windows 2012 R2 domain controllers
The SIDs are probably exclusively generated if the client identifies at a 2012 R2 domain controller. This is the reason why the problem only occurs occasionally with 2008 R2 DCs and 2012 R2 DCs.
The true reason for the malfunction is the fact that Windows 7 clients do not support the SIDs. It is impossible to process the SIDs correctly.
Understanding the error with PSGETSID
You can reproduce the error by using the command “psgetsid” in a PowerShell or in cmd. Microsoft provides some solution:
PsGetsid.exe is part of PsTools of Sysinternals and you can download it here:
Webseite: PsTools (Sysinternals)
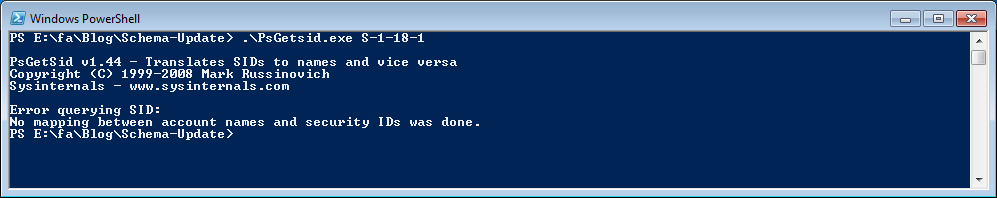
PS E:\fa\Blog\Schema-Update> .\PsGetsid.exe S-1-18-1
PsGetSid v1.44 – Translates SIDs to names and vice versa
Copyright (C) 1999-2008 Mark Russinovich
Sysinternals – www.sysinternals.com
Error querying SID:
No mapping between account names and security IDs was done.
However this does NOT check for actual problems of client.
Checking the client with GPRESULT
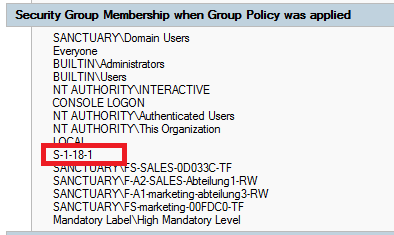
In order to check for problems of a client you should use a bord medium with gpresult /h:
In a list of group member features you find the entry „S-1-18-1“ with the affected Windows 7 clients:
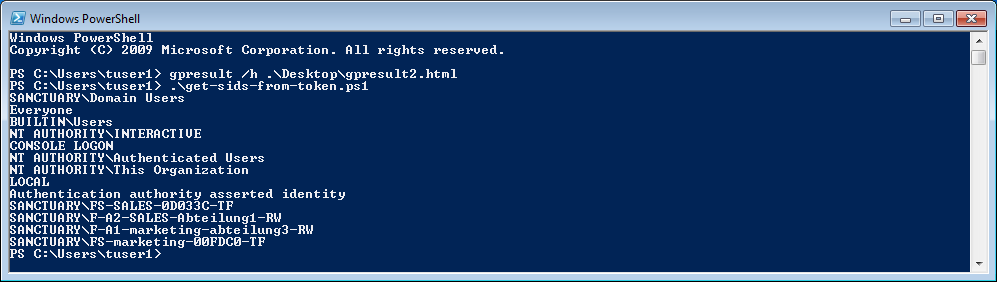
Checking the client with”Get SIDS from Token”
Slightly more elegant to be done in the way described in the last article (Read Kerberos-Token with PowerShell ). The affected clients output the following warning:
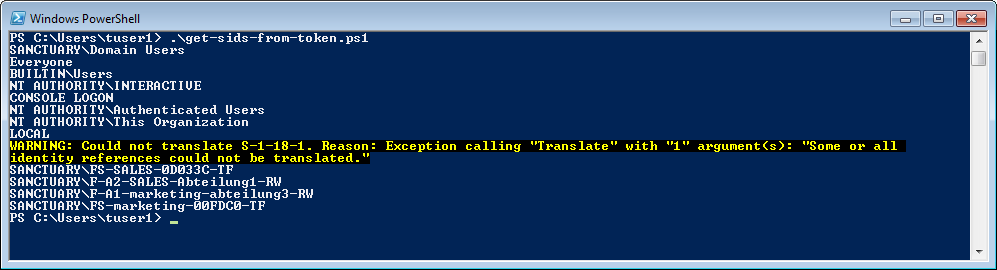
PS C:\Users\tuser1> .\get-sids-from-token.ps1
SANCTUARY\Domain Users
Everyone
BUILTIN\Users
NT AUTHORITY\INTERACTIVE
CONSOLE LOGON
NT AUTHORITY\Authenticated Users
NT AUTHORITY\This Organization
LOCAL
WARNING: Could not translate S-1-18-1. Reason: Exception calling “Translate” with “1” argument(s): “Some or all identity references could not be translated.”
SANCTUARY\FS-SALES-0D033C-TF
SANCTUARY\F-A2-SALES-Section-RW
SANCTUARY\F-A1-marketing-section-RW
SANCTUARY\FS-marketing-00FDC0-TF
Solving the Problems after Schema Update and Hotfix
Microsoft has finally come up with a solution for that problem. Thus they published a hotfix that actually fixes the problem:
https://support.microsoft.com/en-us/kb/2830145
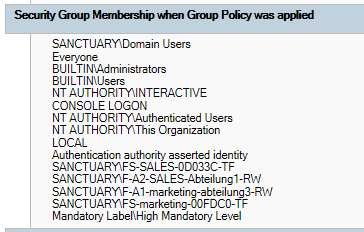
The hotfix was rolled out successfully on the clients of a customer. The problem with the Schema Update was solved. You may want to test if the hotfix worked. So you check this by using the command gpresult /h. The entry “S-1-18-1” should have been deleted:
Now you can test again with “get-sids-from-token.ps1” (detailed information in the link)
Eventually the SID will no longer be listed in the token:
PS C:\Users\tuser1> .\get-sids-from-token.ps1
SANCTUARY\Domain Users
Everyone
BUILTIN\Users
NT AUTHORITY\INTERACTIVE
CONSOLE LOGON
NT AUTHORITY\Authenticated Users
NT AUTHORITY\This Organization
LOCAL
Authentication authority asserted identity
SANCTUARY\FS-SALES-0D033C-TF
SANCTUARY\F-A2-SALES-Section-RW
SANCTUARY\F-A1-marketing-section3-RW
SANCTUARY\FS-marketing-00FDC0-TF
FirstAttribute AG – Microsoft Consulting Partner for
Migration and Active Directory








Leave a Reply
<p>Your email is safe with us.<br/>Information about our <a href="https://activedirectoryfaq.com/contact-us/">data protection policies</a></p>