In its February-Patch, Microsoft covers an important security gap which allows attackers to execute malicious code on user PCs.
It concerns the function for executing batch-files and scripts – e.g. during logon to a client – on all Windows client- and server-systems (since Windows Vista/ Windows Server 2003).
That gap, caused by reloading scripts and executing the malicious code, can be closed by installing the patch and setting the new settings in the group policies “UNC Hardened Access”.
Index
Vulnerability through the remote loading of scripts
A Man-in-the-Middle-attack for remote code execution could look like this:
An attacker suprveils the traffic of a company network. He sees clients requesting a file of the UNC-path \\10.0.0.100\Share\Login.bat during the login.
The attacker then sets up a share on his own machine. The UNC-path is exactly the same to the one the victim uses to requests the file (\\*\Share\Login.bat).
Naturally, the batch-file on the attacker’s machine does not only contain the original function but also some malicious code the attacker want to run on the victims PC.
Finally, the attacker modifies the ARP-table on the respective switch that is responsible for the resolution of addresses in the network.
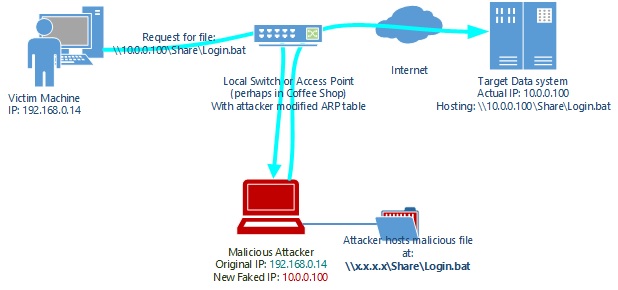
Man-in-the-Middle Attack | Source: Microsoft
For the next login, the batch will be requested form the machine of the attacker. It will then be executed via the local user account or even the SYSTEM-account and can give the attacker access to the system.
The attacker could:
- Install programs
- Delete or manipulate files
- Or even set up new user accounts with administrator permissions.
Group Policy: UNC Hardened Access
To prevent such a “Man-in-the-Middle”-attack, Microsoft introduced UNC Hardened Access as a group policy with Patch KB3000483. Different settings ensure that the client always checks the identity of the server during UNC requests. Thus, Man-in-the-Middle-attacks can be identified and exposed.
This, however, cannot be achieved by only installing the patch.
How to set up Hardened UNC Access
The function is deactivated by default and has to be configured by an admin. For this, proceed as follows:
- Install the security-update directly via Windows Update or download the respective version via Microsoft’s Download Center.
- Log in to the server with administrator-rights and open the console for the administration of group policies. Navigate the left tree to the required domain and select the group policy-object you want to edit. Open the context menu and select
- Navigate the editor-console for the group policy object to the path Computer Configuration/Administrative Templates/Network/Network Provider. There you can find the new setting Hardened UNC Paths. Reopen the context menu and select Edit
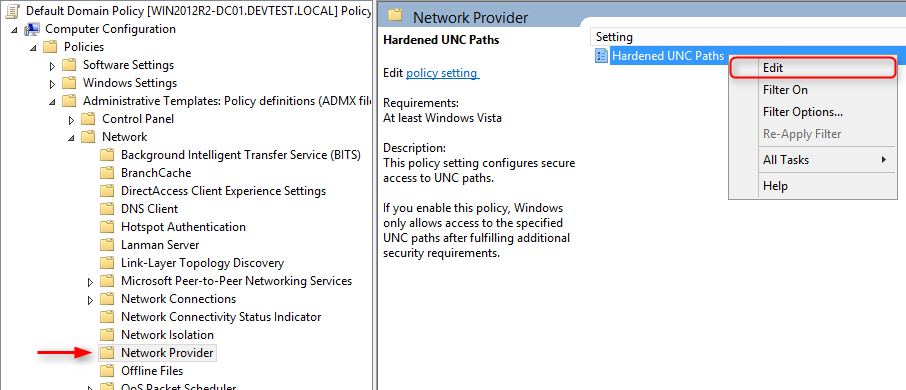
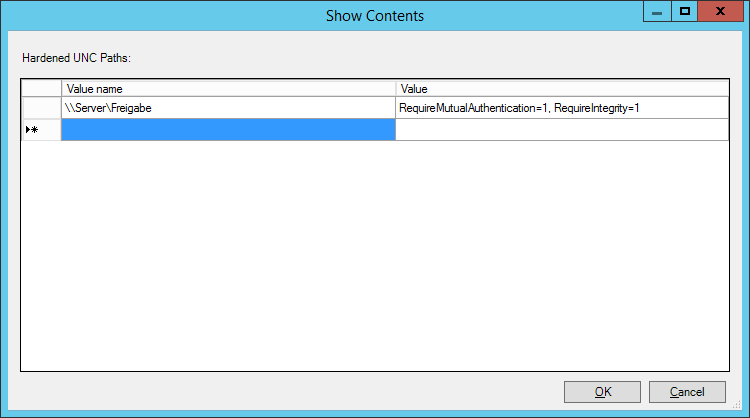
- Activate the option box Enabled in the settings to activate the hardened UNC-paths. To select which checks should be run, scroll down to the Show-button in the area Options and check it.
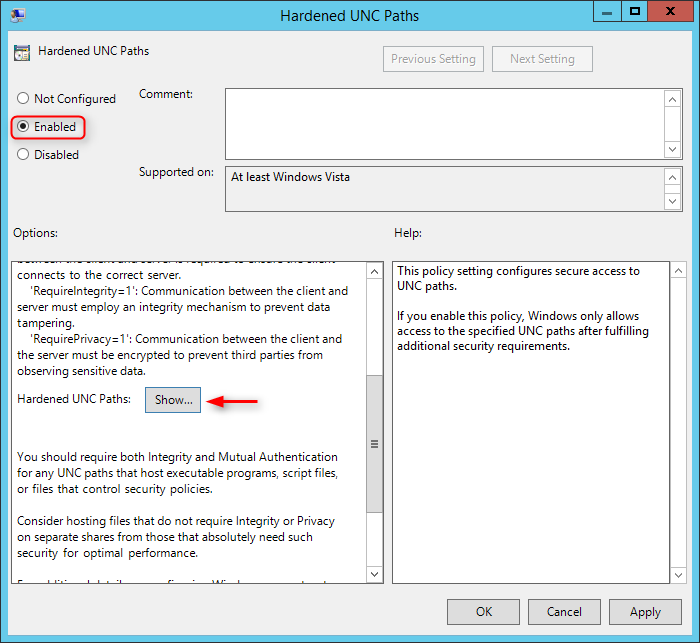
- A table will open where you can enter a UNC-path into the left and an option valid for this path into the right column. The UNC-path has to be in one of the following formats
- \\<Server>\<Release>: The configuration entry is valid for the release which has the indicated name on the indicated server.
- \\*\<Release>: The configuration entry is valid for the release which has the indicated name on any server.
- \\<Server>\*: The configuration entry is valid for all releases on the indicated server.
In the column Value on the right side, you can choose between three options for each entry.
- RequireMutualAuthentication=1: The UNC-provider requests to be able to authenticate the identity of the remote server. By this additional identification of the server towards the client, Man-in-the-Middle-attacks can be prevented.
- RequireIntegrity=1: Client and server use check sums to guarantee data integrity and prevent manipulation.
- RequirePrivacy=1: Client and server have to use an encryption method which prevents third parties with reading rights from reading the communication contents.
These settings can explicitly be deactivated for specific UNC paths by setting 0 instead of 1. Multiple settings can be separated by a comma.
- To confirm your entries, click OK twice. Test your settings on a PC for which the edited group policy object is valid. Log on to the PC and execute the command gpupdate /force in the console. Possible errors can be found in the Event Viewer afterwards under Event Viewer\Application and Services Logs\Microsoft\Windows\Networkprovider\Operational.
To ensure the security of the company network and its computers, it is recommended to run the updates for all group policys loading batch-files and other scripts via remote servers.
Links
Microsoft Summary February Patch
Weitere Informationen zum Thema:
Technet: Securtiy gap & hardening GPO
Microsoft Support website for Hardened UNC Paths







Leave a Reply
<p>Your email is safe with us.<br/>Information about our <a href="https://activedirectoryfaq.com/contact-us/">data protection policies</a></p>