The following example shows how to set up users in the Active Directory whose name is saved in a SQL-database with the help of PowerShell. The result of the bulk […]
To optimize search results in Outlook, different parameters can be used. The syntax is structured as follows:
|
1 |
Search Operator: search string |
Beside the special search operators you can also use logical operators in […]
Almost every company is using virtual machines today. The advantages: VMs can be drawn up easily. Before important changes you can make snapshots. In case something should go wrong, you […]
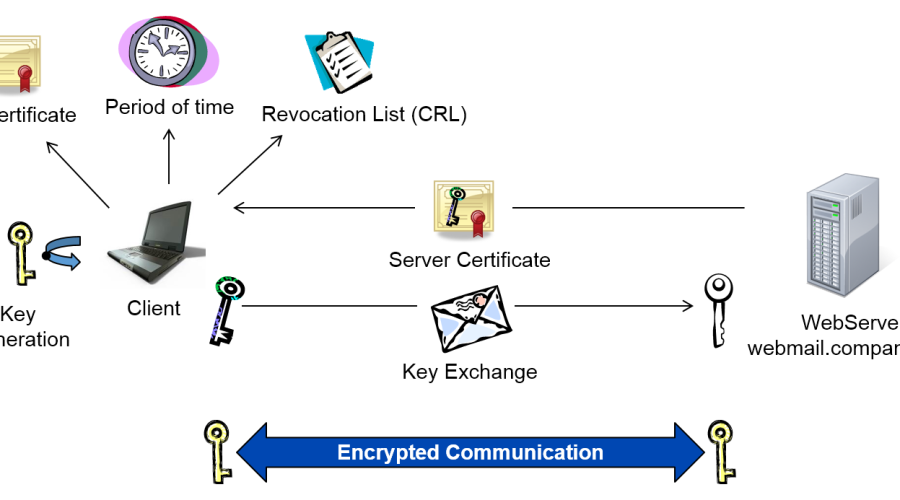
The usage of digital certificates for encrypted communication and lettering of data like email is a top item on most companies’ wish list. Surprisingly many companies still don’t use it. […]
Novell Zenworks is a software suite which consists of various packages. If you want to migrate Novell clients into Active Directory you first of all need to update from Zenworks […]
Event ID 10016 – Solving the DCOM Security Policy message in SharePoint 2010 step-by-step. In the last half year we designed and built a 3-step SharePoint 2010 environment for a […]
Some days ago, I wanted to activate the group policy for the KDC claim support to use Dynamic Access Control. The AD domain consisted of Windows Server 2008 R2 and […]
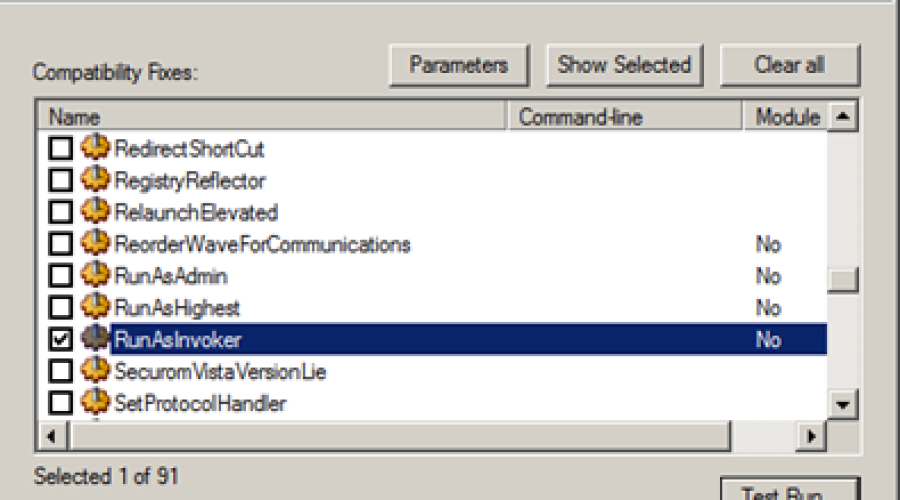
The user account control (UAC) of Windows prohibits system interventions by applications as long as you have not accepted the warning dialog. You can bypass the warning dialog by installing […]
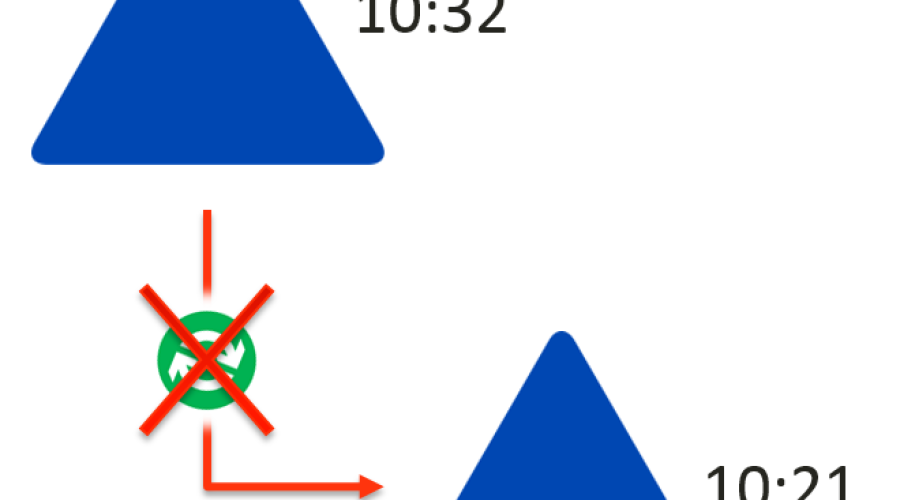
While checking the eventlog of a domain controller I noticed that it complained about an erroneous Kerberos ticket of another DC.As we all know, Kerberos needs a synchronous time of […]
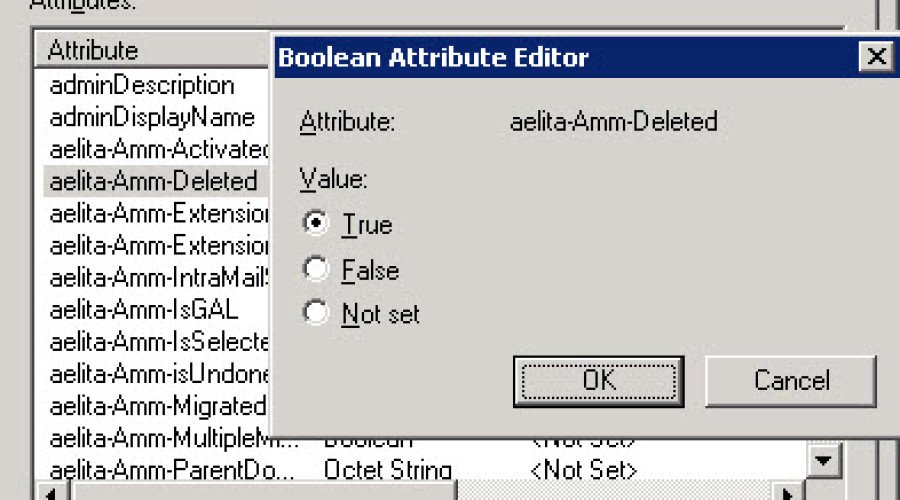
During a directory synchronization with Quest Migration Manager for AD QMM, orphaned objects can be created in the ADAM database. I have repeatedly reported about the handling of Quest Migration […]